Hackers target politicians with fake news website
- Published
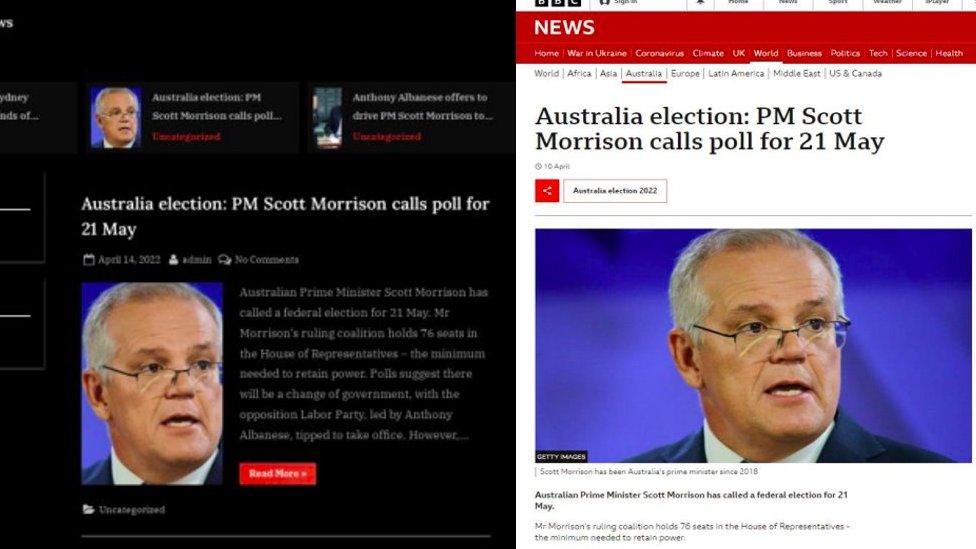
The fake website was populated with articles stolen from BBC News
Hackers created a fake news website to harvest data from Australian government officials, journalists and others, according to a top US security company.
The targets received emails claiming to be from Australian news outlets, which linked them to a malicious website.
The website, populated with articles stolen from BBC News, would then install malicious code on their device.
Proofpoint said it had "high confidence" the hackers were aligned with the Chinese government.
"We take attribution very seriously," Proofpoint threat research and detection vice-president Sherrod DeGrippo said.
"We specifically don't release attribution unless we have high confidence.
"Essentially, a big part of our attribution capability comes from the fact that the United States Department of Justice agrees with the attribution and data that we have released.
"The reason that we have such high confidence in this particular attribution really goes back to the DoJ indictment, which mentions these defendants and specifically calls out the Proofpoint name identifier of 'Leviathan'."
'Espionage-motivated threat'
Proofpoint said the hackers were part of a group of which four members had been charged by the US in 2021, when the UK's National Cyber Security Centre said it was "almost certain" they were linked to the Chinese government, external.
It said, external the group was "a China-based, espionage-motivated threat actor that has been active since 2013, targeting a variety of organisations in response to political events in the Asia-Pacific region, with a focus on the South China Sea."
The Australian Cyber Security Centre has been approached for comment.
In the group's latest hack, between April and June, victims had received emails claiming to be from someone who had started a news website, Proofpoint said.
They had then been asked to review the site and consider writing for it.
'Anglo-styled names'
"What I think is quite novel about it is they went so far as to create these fake media websites, by scraping legitimate sites, including the BBC, in their efforts to appear real," Ms DeGrippo said.
"And further, they created multiple identities that they were sending from.
"There's about 50 of them... all of the very Anglo-styled names you might imagine Australians to be named.
"They created all of these sorts of pseudo identities to launch the attack from, making them more believable."
The fake names - each with their own unique Gmail address - included Daisha Manalo, Blair Goodland, and Bethel Giffen.
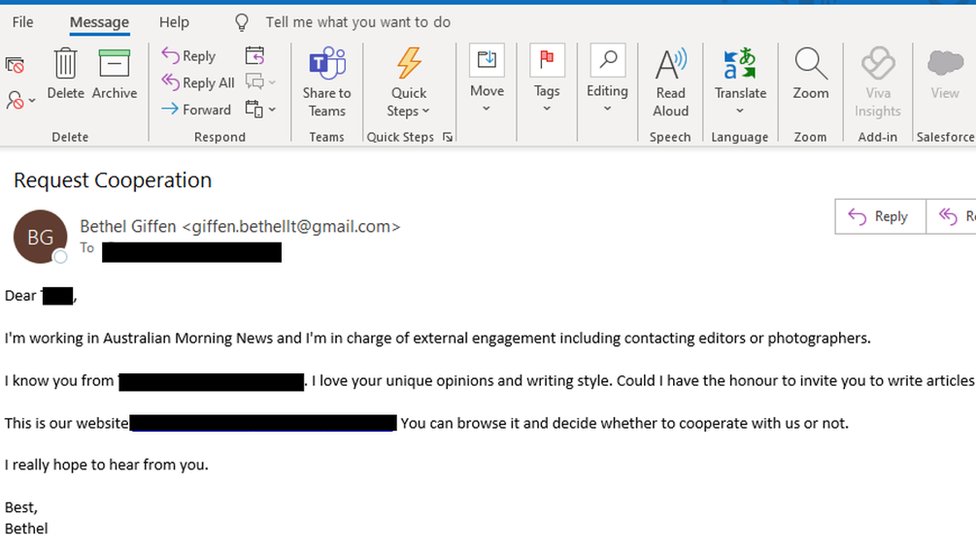
Victims were invited to write for a new news website, which was fake
The fake website was filled with malware that would infect the victim's computer with a tool called Scanbox, checking their profile, device and web pages visited.
"Scanbox essentially is a web reconnaissance and exploitation framework," Ms DeGrippo said.
"When we think about that, in conjunction with the actor who is a China-based espionage group, it makes sense."
'Sensitive role'
The attack seemed to focus on people involved in energy production, such as offshore energy exploration in the South China Sea, wind-turbine manufacture and alternative energy but also defence contractors and individuals involved in healthcare and financial services.
"Consumers generally are not on the radar of Chinese espionage services," Ms DeGrippo said.
"However, anyone who has a sensitive role within their professional employment, even if they're dealing with things such as engineering, things that might not seem like state secrets... the reality is China sees them as secrets and as important espionage information."
People should ensure their browsers were updated and firewall and antivirus software turned on, Ms DeGrippo said.
But she added: "Organisations professionally must think about the kinds of data that their employees have access to and if they have the correct technological means in place to protect their employees from these kinds of attacks.
"By the time it gets to a human, it's really too late."
- Published19 August 2022

- Published31 August 2022

- Published26 August 2022
