Gawker hack triggers password resets at major sites
- Published
Millions of web users are being asked to reset their passwords as concerns spread over a major hacking attack.
Yahoo, Twitter and LinkedIn have asked users to change their details, days after gossip site Gawker was hacked.
Online game World of Warcraft, which has more than 12 million subscribers, has also asked some users to reset their passwords.
Blizzard, the company behind the game, said it was an attempt to "minimise the effects" of the Gawker breach.
Although thousands of Twitter accounts were compromised after the attack, there have been few other reports of damage directly linked to the breach.
Many companies, however, have taken steps to identify users at risk and warn them before an exploit can take place. A spokesman for LinkedIn said it necessary to take "proactive security measures" to screen users thought to be in danger.
Defence mode
The attack on Gawker, which runs one of the world's most popular blog networks, was carried out over the weekend by an organisation calling itself Gnosis.
The group - which says it was making a protest at the site's perceived "arrogance" - subsequently published account details of 1.3 million Gawker users online, including a significant number of passwords.
Analysis of the breach has triggered a widespread defensive response because it emerged that many users had chosen common words and codes that left them wide open to abuse.
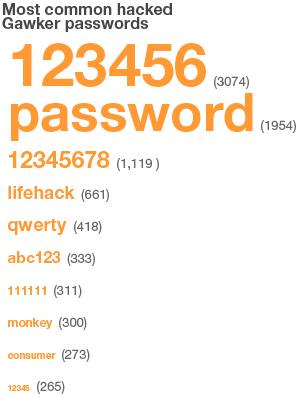
Documents show that the most popular password among Gawker users was "123456", followed by "password" and "12345678".
Other common terms, used by hundreds of people, included "monkey", "qwerty" and "consumer".
Although security experts warn against the use of passwords that are easy to guess, research suggests such behaviour is increasingly common online.
According to a study by computer security company Sophos, external, 33% of people admitted using the same password for every single website they visit.
A further 48% said they used just a handful of different codes, while just one in five said they never used the same password twice.
The firm's Graham Cluley said that the domino effect evident among web companies exposed a number of significant issues.
While it was important to remind users that their passwords should be changed regularly, he said, the warnings sent out to users did not always address the central issue of poor password choices.
"The bad guys already have databases of the most common passwords, and they look a lot like this," he said.
"It's no bad thing to try and help, but websites should give users more information about how to create a secure password."
- Published13 December 2010
- Published10 June 2010