Exposing Russia's murky trade in exploit hack packs
- Published

Exploit packs, such as Crimepack, are usually only sold to known hackers
Russian computer programmers have created an industry supplying criminals with easy-to-use automated hacking software which can take control of a home PC in seconds.
This type of software, called an exploit pack, takes advantage of known flaws in commonly used programs, such as Adobe Reader and Internet Explorer, to hack computers without the need for human intervention.
Criminals are then able to install viruses or steal online banking details without the need for any technical expertise.
The exploit pack market mimics the market for legal software, with vendors offering criminals trial periods, regular updates and even 24-hour technical support.
Software licences of varying lengths are available to suit the needs of different hackers: A one year licence costs about $1,500 (£968), a six-month licence about $1000, or a three-month licence just $700.
Supply and demand
Some sellers also offer their exploit packs as a service, running and managing them on their own servers and renting out access to criminals for about $500 per month or $200 per week.
Some of the exploits in the kits target Linux and Mac-based systems, but most are directed at Windows machines.
Fyodor Yarochkin, a security analyst at California-based Armorize Technologies, says the programmers who create the packs are simply filling a gap in the market.
"Criminals want exploit packs, so these people provide them," he says.
They are mostly professional programmers who previously had legitimate jobs with large companies, but who prefer to work for themselves and earn a little more money, he believes.
Some are also computer science students.
"We discovered one exploit pack developer who also had research published on a university web site," Mr Yarochkin said.
Marketing
Since most exploit packs have broadly the same capabilities, the creators put a great deal of effort into designing their products' user interfaces to make them as attractive-to-look at and as easy-to-use as possible.
They are usually given English language names. Some are sinister, like Crimepack, Infector and Blackhole. But some are more poetic, like Phoenix and Eleanor, and some charmingly innocent, like Nicepack.
The software is advertised for sale in underground hacking forums, most of which can only be joined if vouched for by an existing member.
To make use of an exploit pack, a hacker first needs to hack a popular legitimate web site, or pay someone else to do hack it on their behalf.
Once the web site has been hacked, visitors to the site are redirected without their knowledge to the computer running the exploit pack.
This will then attempt to take control of the visitor's computer, and if successful load a virus or other malicious software on to it.
Unaware
Research conducted by CSIS, a Danish security company, suggests that the overwhelming majority of virus infections - about 85% - are the result of the work of exploit packs.
If the software works as it is designed to then the whole process may happen invisibly, according to Alen Puzic, a security researcher at Texas-based Tippingpoint Dvlabs.
"A victim would continue their web browsing and may never know that they have been hacked," he says. But occasionally there may be some hint that a computer has been compromised.
"In some cases, an exploit pack doing its job might cause a victim's browser to crash, or something unexpected might happen," Mr Puzic adds.
"For example, Blackhole exploits a vulnerability in Windows Media Player, so if Windows Media Player suddenly starts up on your computer for no apparent reason, then that would be a tell-tale sign of an attack."
CSIS estimates that exploit packs successfully take control of about 30% of the computers that are redirected to them.
But almost all of the software flaws that the packs take advantage of are well known and have been fixed in the latest updates to the software concerned, so protecting yourself against them is very easy, Mr Puzic says.
"If you patch and update all the software on your computer then you are simply not vulnerable to exploit packs. They only work because most computer users don't update their software as often as they should."
Add-ons
Prices for exploit packs have dropped in recent months, due in part to software piracy. Unlicensed copies of some packs have been leaked on some hacker sites.
A few sellers have also started to give away outdated versions of their packs as promotional tools. To compensate for falling sales revenues, many vendors are now offering additional services for an extra fee.
One such service runs a criminal's virus through a suite of all the leading anti-virus programs to check whether any of them can detect it. If they can, then the virus can be modified and resubmitted until it evades detection.
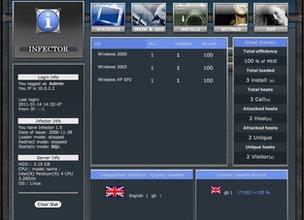
The creators of exploit packs try to distinguish their products by designing different user interfaces
This type of service typically costs $2 or $3 a time, or around $50 for an unlimited monthly pass.
Vendors also monitor the blacklists compiled by anti-virus companies which contain the addresses of servers known to be running exploit packs, and offer criminals new addresses if theirs get blacklisted - for a fee of about $50.
Bashful
Do exploit pack authors believe that what they do is wrong?
That is hard to answer because, while they imitate many aspects of the legitimate software market, it seems they draw the line at talking to the media.
When contacted using an online chat service for this article, an individual describing himself as a "programming engineer" for the Blackhole exploit pack initially expressed enthusiasm for the exposure, writing: "Cool. I star (lol)."
But he then changed tack, declining to answer any questions.
"Sorry I do not give interviews," was his only comment, before quickly disappearing.
- Published24 November 2011
- Published29 March 2011
- Published5 April 2011