LinkedIn users targeted in email scam after hack
- Published
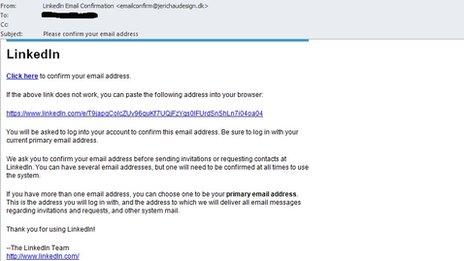
Convincingly-designed emails like these have been sent to LinkedIn users
LinkedIn users have been targeted by email scams after hackers leaked more than six million user passwords online.
Emails designed to look like they were sent by the social-network website asked users to "confirm" their email address by clicking a link.
However, the link took unsuspecting recipients to a site selling counterfeit drugs.
Dating website e-Harmony has also admitted that a "small fraction" of its users' passwords have been leaked.
The scam emails appear to have been widely distributed. Some internet users who were not members of the site have reported receiving them.
Password reset
Approximately 1.5 million passwords from the US-based relationship site were posted online, reported <link> <caption>Ars Technica</caption> <url href="http://arstechnica.com/security/2012/06/8-million-leaked-passwords-connected-to-linkedin/" platform="highweb"/> </link> .
The company said on its blog that it had reset the passwords of the affected users, who would receive an email with instructions on how to set new passwords.
On Wednesday it was revealed that 6.4 million passwords from LinkedIn had been posted on a Russian web forum, along with a message encouraging other hackers to help decrypt the " <link> <caption>hashed</caption> <url href="http://en.wikipedia.org/wiki/SHA-1" platform="highweb"/> </link> " data.
Affected LinkedIn users have been told they will receive instructions in an email - but not with a link - on how to change their details.
How to change your LinkedIn password
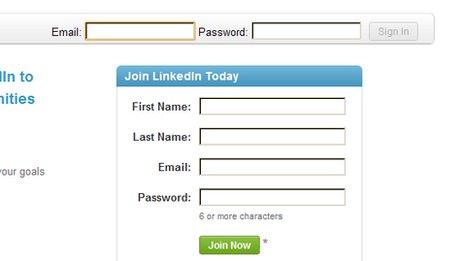
Security experts have advised users to change their passwords on LinkedIn. Here's how: First, visit www.linkedin.com, and log in with your details
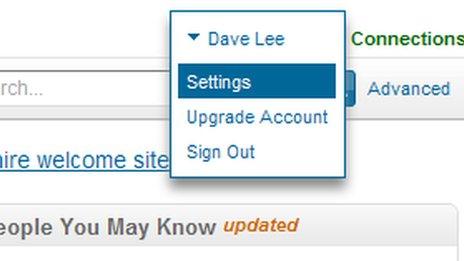
Once logged in, hover over your name in the top right-hand corner of the screen, and select Settings from the menu
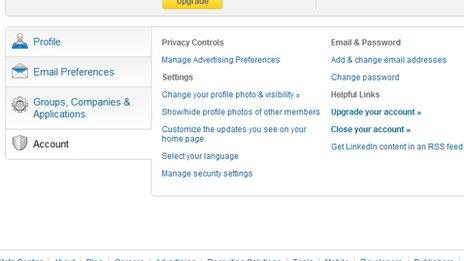
On the next screen, click the Account tab, found near the bottom left-hand side of the page
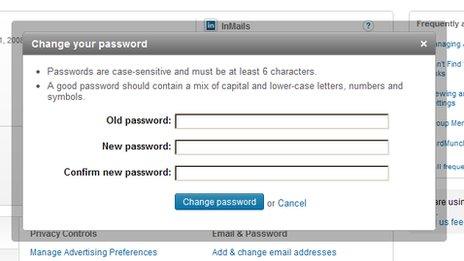
Under the Email & Password heading, you will find a link to change your password. If you use the same passwords on other sites, change those too
"Members that have accounts associated with the compromised passwords will notice that their LinkedIn account password is no longer valid," said LinkedIn director Vicente Silveira, confirming that a breach had occurred.
He added: "These members will also receive an email from LinkedIn with instructions on how to reset their passwords.
"These affected members will receive a second email from our customer support team providing a bit more context on this situation and why they are being asked to change their passwords."
However, Ant Allen, from analyst firm Gartner, said LinkedIn must do more to inform their members about the situation.
"I'd really like to see a clearer statement from them on their front page," he told the BBC.
"A statement that they were taking steps to minimise the risks of passwords being exposed in the future and the risks to users if passwords were exposed would do a lot to reassure people. Simply saying, 'we need you to reset your password as a security precaution' is not enough."
Final tally 'higher'
Security analyst Imperva said it believed the breach was larger than had been acknowledged, as the list did not duplicate individual passwords, even though many were likely to have been used by more than one user.
"The list doesn't reveal how many times a password was used by the consumers," the company said.
"This means that a single entry in this list can be used by more than one person. For reference, in the [social network] RockYou hack the 5,000 most popular passwords were used by a share of 20% of the users. We believe that to be the case here as well, another indicator that the breach size exceeds 6.5m."
The password breach came just hours after the company admitted it had updated its mobile apps due to a privacy flaw.
In a blog post, Skycure Security said the the mobile app was sending unencrypted calendar entries to LinkedIn servers without users' knowledge.
In response LinkedIn said it would "no longer send data from the meeting notes section of your calendar".
- Published7 June 2012
- Published4 May 2012