Shape-shifting software 'defends against botnet hacks'
- Published

Shape Security says its product makes it harder to carry out automated attacks
A technology that constantly changes websites' code to defeat hackers has been unveiled by a US start-up.
Shape Security says its product works with the HTML, JavaScript and CSS languages, transforming a site's code into a "moving target" to prevent cybercriminals from carrying out scripted attacks.
The Silicon Valley firm has several high-profile backers including Google.
But one expert said hackers might still be able to work round the defence.
However, Ron Austin - a senior lecturer on computer security at Birmingham City University - said that it would probably take them longer than previously.
Shape says the "look and feel" of the sites that use its tech remains unchanged to legitimate visitors.
It adds that several companies have already trialled its product, including Citigroup bank and the ticket seller StubHub.
Morphing code
Shape describes its product as a being a "botwall" - a reference to it being a barrier against automated software tools known as bots that recognise and exploit vulnerabilities in a site's code.
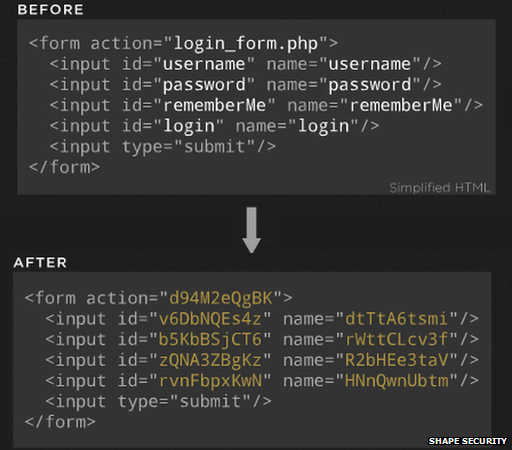
ShapeShifter aims to alter how code is expressed without affecting its functionality. In this example, a login form has certain attributes replaced with random strings, with new code generated for each page request. The firm says this is a "simplified example" created to illustrate one of the polymorphic techniques it uses, and that the real output would be different
These can be used for malicious purposes, such as carrying out DDoS (distributed denial of service) attacks - forcing a website server to crash by flooding it with traffic - or to hijack a site, allowing the hacker to modify its contents, steal private details and spread malware.
Many products try to prevent such breaches by identifying bots by their signatures - the name they use when registering themselves - and the internet and email addresses they send data to.
Hackers have tried to counter detection by using a technique called "real-time polymorphism" - making their bots rewrite their own code every time they infect a new machine to make them harder to recognise.
Shape says its product reverses this advantage.
"The website looks and feels exactly the same to legitimate users, but the underlying site code is different on every page view," wrote the firm's founder, Sumit Agarwal, on its blog, external.
"Ultimately, the ShapeShifter aims to stop non-human visitors from executing large-scale automated attacks. This may help break the economics of breaches like the one Target experienced in late 2013, by eliminating the monetisation path.
"Without automated scripts, many of today's attacks cease to be economically viable."
'Additional tool'
Shape had raised $26m (£15.7m) from investors ahead of its product's launch.

Shape says several firms have been secretly testing its equipment ahead of the launch
Backers include:
Google Ventures, the search firm's venture capital fund
Google chairman Eric Schmidt's personal investment company TomorrowVentures
Kleiner Perkins Caufield & Byers, an early investor in Amazon and Facebook
Enrique Salem, the former chief executive of security firm Symantec
One security expert from the University of Oxford's Internet Institute said the innovation sounded promising.
"It's an interesting additional tool for making it harder for attackers to break into systems, and one that can't be trivially circumvented by attackers changing their behaviour," Dr Ian Brown told the BBC.
But Ron Austin added that given enough time, a dedicated hacker should still be able to achieve their goal.
"The caveat to this approach would be looking for parts of the polymorphic code within the software that does not change," he explained.
"This would then give the attacker a point of reference into the system and possibly allow a new attack to be created. This is difficult and would take time as the attacker would have to monitor the software."
- Published12 December 2013
- Published8 January 2014
- Published9 October 2013
- Published5 December 2011