Horizon: The defenders of anonymity on the internet
- Published
WATCH: University of Oxford's Dr Joss Wright introduce internet anonymity pioneer David Chaum in this clip from Horizon: Inside the Dark Web
You may not realise it, but every time you open up your laptop or switch on your phone, you are at the heart of one of the greatest battles now taking place in our midst - what shape will the internet take in the future, and what role will anonymity play in deciding it?
Last year, the revelations of US security contractor Edward Snowden, suggested for the first time the extent to which governments were collecting and analysing our communications over the internet.
But what Horizon reveals is that scientists are growing increasingly concerned about the way such information could be used to predict our behaviour and from that, be used as a form of control.
"The power of that data to predict and analyse what we're going to do is very, very high," says Dr Joss Wright of the Oxford Internet Institute. "And giving that power to somebody else, regardless of the original or stated intentions, is very worrying."
What Dr Wright is talking about is "traffic analysis", which allows the prediction of the behaviours of individuals, not by looking at the contents of their emails, but by looking at the patterns of communication.
It's become ever more possible as we spend more of our lives online. However, what few may realise is that scientists at the dawn of the information age predicted such issues would eventually become matters of public concern and interest.
Godfather of anonymity
Few outside the computer scientists' community will know the name David Chaum, yet he has a claim to be one of the great visionaries of contemporary science.

The Snowden leaks suggest the NSA and GCHQ monitor large amounts of the public's online activities
In the early 1980s, while a computer scientist at Berkeley, Chaum predicted the world in which computer networks would make mass surveillance a possibility.
As Dr Wright explains: "David Chaum was very ahead of his time. He predicted in the early 1980s concerns that would arise on the internet 15 or 20 years later."
This visionary thinker now rarely gives interviews, but he has spoken exclusively to Horizon about his early work and his anxieties about the world we live in today.
"Well it's sad to me," he explains.
"But it is really no surprise that the privacy issue has unfolded the way it has. I spelled it out in the early publications in - in the 80s."
Chaum's great achievement is that he didn't simply identify the problem, he developed prototype systems that would make such surveillance more difficult.
The most important being something called a Mix Network which used sophisticated cryptography not to encrypt the content of message but to hide the identity of the user. As Chaum himself admits, "this was quite a paradigm shift".
Chaum's insights have given him the unofficial title of "the godfather of anonymous communication" because, amongst other things, his systems provided the theoretical basis for the modern Tor network.

Tor began life as a project at the US Naval Research Laboratory and its developers still receive funds from the US government
Developed by the US Government in the early 2000s, Tor made it possible to browse the net anonymously.
Its ability to allow individuals to operate online without detection has proved a vital tool for dissidents in regimes which operate close control of the online space, such as Syria, Iran and China.
Yet it has taken off in the West in a way the US government never imagined - for whistleblowing against the US itself.
'Real autonomy'
In 2011, it is believed that Chelsea Manning used Tor to leak US government cables and other data to Wikileaks which constituted one of the greatest government leaks in history.
Horizon has gained access to the Ecuadorian embassy for an in-depth interview with Julian Assange who, while refusing to comment on Manning, agrees that Tor was important to Wikileaks.
"It was a longstanding quest… to be able to communicate individual to individual freely and anonymously," Assange says.
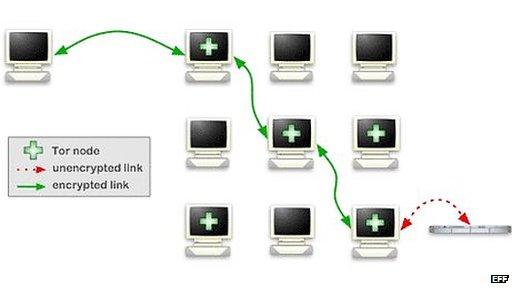
Tor hides a user's identity by routing their traffic through a series of other computers
"Tor was the first anonymous protocol to get the balance right."
Yet Tor's effectiveness has also made it a target for the US National Security Agency, that has made repeated attempts to attack it.
Campaigners like Jacob Appelbaum, who has worked with both Wikileaks and Tor, condemn these actions.
"They want to attack people and sometimes technology makes that harder… the users have something which bothers them which is real autonomy… true privacy and security," he says.
Yet while anonymity offers a potential bulwark against surveillance, for those who do not wish to be watched, it has also helped in the development of that part of the online world known as the dark web.

Julian Assange's Wikileaks suggests whistleblowers use Tor to pass it information
Sites on the dark web like Silk Road have used Tor technology to hide their location and yet still be available to users who wish to visit them.
The dark web has now become a focus for law enforcement officers who believe it is facilitating a variety of illegal activities including financial crime and child abuse.
"Our detection rate is dropping" says Troels Oerting, head of Interpol's cybercrime centre.
"It's risk-free crime."
The arguments over illegality aside, many believe we need to develop technologies which make everyday use of the internet more resistant to surveillance and for that, we need to be able to encrypt our content.
Encryption is, as Edward Snowden has said, the "defence against the dark arts for the digital realm".
Yet currently, many encryption products, including Tor are not user-friendly enough.

Tor, I2P and Freenet are three of the best-known anonymising networks
There is some consensus that the market will need to provide the necessary solution - and for those who wish to avoid surveillance - the outlook is hopeful since, as Julian Assange points out: "It turns out that it's easier in this universe to encrypt information, much easier than it is to decrypt it if you're someone watching from the outside... the universe fundamentally favours privacy."
The question now is whether there is sufficient public interest and pressure to make that encryption the norm rather than the exception.
UK viewers can watch Horizon: Inside the Dark Web on BBC Two at 21:00 and on iPlayer afterwards.
- Published22 August 2014

- Published30 July 2014

- Published23 July 2014
