HTC phone stored unencrypted fingerprints
- Published

The HTC One Max was released in October 2013
Security researchers have identified a way to access unencrypted fingerprint data on an HTC smartphone.
Four experts from security company FireEye found the HTC One Max stored fingerprint data in an image file that was simple to decode.
A growing number of smartphones use fingerprint recognition to unlock the device or authorise online purchases.
HTC did not respond to a request for comment but the BBC understands the flaw has now been fixed.
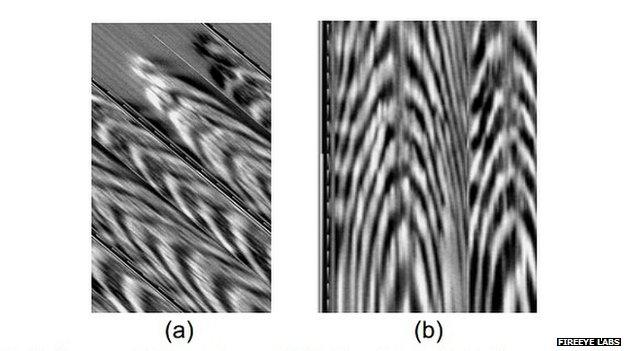
The phone's fingerprint data (a) was easily converted back into a fingerprint (b)
Recognising biometric data such as a fingerprint or face is a convenient way for people to interact with their handset, but security experts continue to question its long-term practicality.
"Biometric data is personal, it's an image of my fingerprint," said Professor Angela Sasse from University College, London.
"It's not beyond the wit of an attacker to create a dummy finger, if they have the raw data. And if they steal my fingerprint, I can't change it."
Prof Sasse said storing a fingerprint in an unencrypted format was "like writing your password on a notepad".

The HTC One Max stored fingerprint data in a "world readable" format
"Good manufacturers should hire a specialist to do a penetration test on their phone before they release it," she said.
"I find it hard to believe they did a security test on this device. And if one fingerprint system is broken, it has a knock-on effect on consumer confidence."
The four researchers - Yulong Zhang, Zhaofeng Chen, Hui Xue and Tao Wei - presented their findings at the Black Hat conference, external in Las Vegas.
They told HTC in advance of their presentation, giving the company time to fix the problem.
The group said people should always keep their phone operating system up to date to protect themselves from known security issues.
- Published7 August 2015
