Questions for TalkTalk
- Published

When the news broke on Thursday evening of a major cyber attack it came from the company itself and TalkTalk appeared eager to be as open as possible. Its chief executive Dido Harding toured the radio and TV studios and was frank enough to admit what she did not know, as well as what she did.
But over the weekend the truth about the extent of the attack became rather less clear. Both customers and security analysts are seeking answers to a series of questions.
How did it happen?
The company first indicated that the "sustained" attack was a DDoS, a distributed denial of service attack where a website is bombarded with waves of traffic. That did not seem to explain the loss of data, and later TalkTalk indicated that there had also been what is known as an SQL injection. This is a technique where hackers gain access to a database by entering instructions in a web form. It is a well known type of attack and there are relatively simple ways of defending against it. Many security analysts were stunned by the idea that any major company could still be vulnerable to SQL injection.
How much data was lost?
On Saturday TalkTalk said the attack had been less serious than it had initially feared. It had been directed at its website and not its core systems, and only partial credit card numbers were available to the hackers. The company told customers that the financial information leaked "would on its own not enable a criminal to take money from your account". But what we still don't know is exactly how much data was encrypted - Dido Harding admitted on Friday she could not be sure - and how many people are at risk.
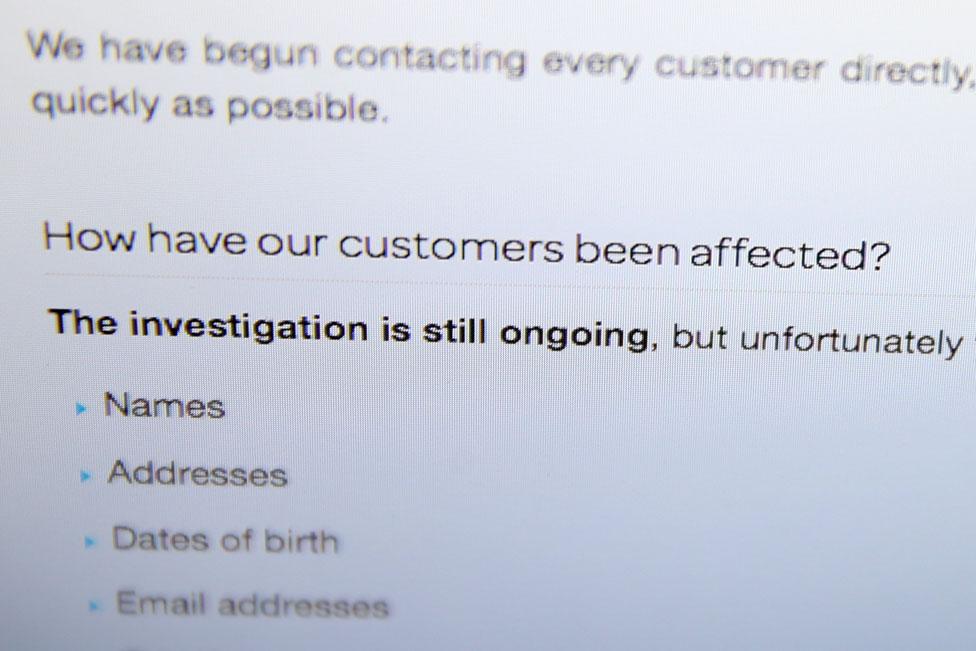
What dangers do customers face?
We are already receiving a number of reports of people having had their bank accounts cleared out, even though TalkTalk says the criminals could not do that with the hacked data alone. It does appear that in most cases the victims received phone calls from scammers armed with other details about their TalkTalk accounts and were then tricked into handing over their banking details.
On Thursday evening TalkTalk said all 4 million customers could be at risk. I've been told by one security source that the database which was accessed contained details of people who had recently undergone credit checks for new services, and that is about 400,000 people. But anyone who has ever done business with TalkTalk or the companies it bought still needs to be wary.

Dido Harding, chief executive of TalkTalk
Who is in charge of TalkTalk security?
The only person speaking on the record about the attack is the chief executive Dido Harding, and obviously the buck stops with her. But she should be receiving information and advice from her security team, and the confused messages about encryption and the nature of the attack seem to indicate that something has gone wrong there.
We know that the company's Chief Information Officer left to join the Police ICT company in the summer, and I am told that a number of other quite senior IT staff have left in the last year. In an unfortunate piece of timing, the company advertised for an Information Security Officer, external earlier this month, but it is not clear who is responsible at a high level for the security of its network.
According to people in the security community, more companies handling vast amounts of sensitive consumer data are now appointing a Chief Security Officer. The role of CSO may become a vital one for public companies in the future.
Could it have happened to any firm?
The idea that TalkTalk is just one victim of a cyber crime wave affecting every industry is one that has been heavily promoted by the company. It is obviously the case that the threat is on the rise, and some very big names have been hit, from Sony to Target to JP Morgan Chase. But what we've learned so far indicates that the TalkTalk attack is not a sophisticated assault by a nation state or organised crime, but a crude stick-up from crooks demanding a ransom to go away. What's more, it is the third such attack TalkTalk has suffered this year. Rebuilding its reputation with customers and security analysts is going to be a lengthy job.