Inside the TalkTalk 'Indian scam call centre'
- Published

TalkTalk has warned its customers to be on the alert for scammers
TalkTalk customers are being targeted by an industrial-scale fraud network in India, according to whistleblowers who say they were among hundreds of staff hired to scam customers of the British telecoms giant.
The scale of the criminal operation has been detailed by the three sources, who say they were employed by two front-companies set up by a gang of professional fraudsters.
The sources describe working in "call centres" in two Indian cities.
They say as many as 60 "employees" work in shifts in each office, phoning TalkTalk customers and duping them into giving access to their bank accounts.
The whistleblowers say they were given a script in which they were told to claim they were calling from TalkTalk.
They say they then convinced victims to install a computer virus.
A separate team would use that virus to gain access to victims' online banking, they add.
While it has not been possible to independently verify their claims, the sources have given highly detailed accounts of the scammers' tactics, which correlate very closely with previous reports of fraud targeting TalkTalk customers.
The software they named also matches that identified by TalkTalk, external in its own website guidance on what to watch out for in a scam call.
In addition, a victim of the fraud shown the call centre script has confirmed it matched the one read out to her when she was conned out of £5,000.
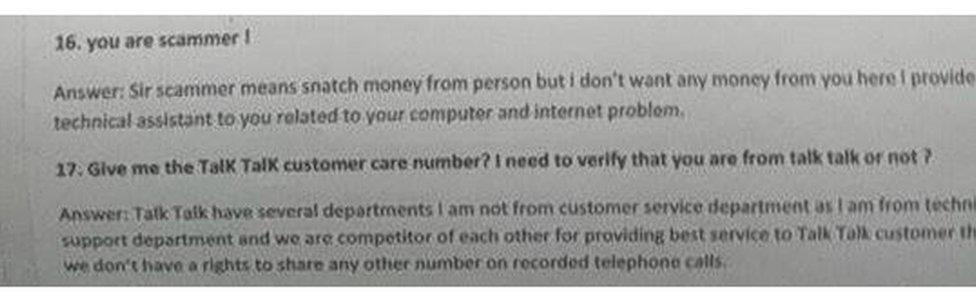
One of the whistleblowers shared this screenshot of one of the scripts
TalkTalk was hit by a cyber-attack in October 2015, but that hack appears to be unrelated to the Indian fraud.
Instead, it is alleged the scam is linked to problems in a company hired by the British broadband provider.
In 2011, TalkTalk outsourced some of its call-centre work to the Kolkata (Calcutta) office of Wipro, one of India's largest IT service companies.
Last year, three Wipro employees were arrested on suspicion of selling TalkTalk customer data.
A source in Kolkata, who did not want to be named, alleges the same data was obtained by a criminal gang, with USB sticks full of data trading hands at parties.
The criminals then used the data to operate at least three call centres, according to the whistleblowers, where staff work in shifts earning about £120 per month to perpetrate an intricate but highly successful scam.
They say they phone TalkTalk customers, using the stolen data to convince victims they are genuine employees of the company.
They then convince the victims their computers are infected, and offer to fix the problems.
Through this, the whistleblowers say, the victim is tricked into installing a virus that gives the scammer complete control over their machine.

The leaked scripts indicate workers were told how to fool victims into believing them
The victims are then offered a compensation payment, for which they must log in to online banking, they add.
Thanks to the virus, the fraudsters are able to gain access to the victims' bank accounts when they log in.
They say they use various methods to spirit away the money: in some cases pretending to make erroneous overpayments, then convincing victims to repay the extra amount.
In other cases, victims have said the scammers were able to set up a new payee without their knowledge and transfer the money out of the account directly.

Why the whistleblowers appear credible:
Although the BBC cannot be sure of the whistleblowers claims, the following suggested they were telling the truth:
the three whistleblowers approached us seemingly independently of each other; the information they shared - including the scripts they were told to read out - correlated to a high degree
during extensive online conversations, they revealed in-depth knowledge of the scammers' techniques, much of which is not in the public domain and matches the experience of TalkTalk fraud victims
one of the whistleblowers shared a copy of his driver's licence, confirming his identity
the whistleblowers said they were ignorant of the full scale of the fraud, because the eventual bank account theft was handled by a separate, smaller team in a different office
at one stage, two of the whistleblowers attempted to share the information of UK victims they had called, and asked us to warn the victims before they fell for the scam

Dozens of customers are said to have been affected, and many have lost thousands of pounds as a result of the fraud.
Leigh Day solicitors is representing about 20 people who have between them lost almost £100,000.

The scripts suggest TalkTalk customers were told that inaction would cause their computers to stop working
Questions remain about the speed with which TalkTalk responded to the data breach at Wipro, which is believed to have been in late 2014.
It was only in October 2015, after the apparently unrelated cyber-attack, that TalkTalk began a "forensic review" leading to the arrests at Wipro.
"We are aware that there are criminals targeting a number of UK and international companies, and we take our responsibility to protect our customers very seriously," said a spokeswoman for TalkTalk.
"This is why we launched our Beat The Scammers campaign, helping all our customers to keep themselves from safe from scammers no matter who they claim to be, while our network also proactively blocks over 90 million scam and nuisance calls a month."
Wipro did not respond to requests for comment.
When contacted, the two companies named by the whistleblowers strongly denied any knowledge of criminal behaviour, and insisted their businesses were legitimate.
Geoff White is a freelance investigative journalist, external, who has also reported for Channel 4 News
- Published7 December 2016

- Published27 January 2016

- Published1 February 2017
