Smart device security guidelines 'need more teeth'
- Published
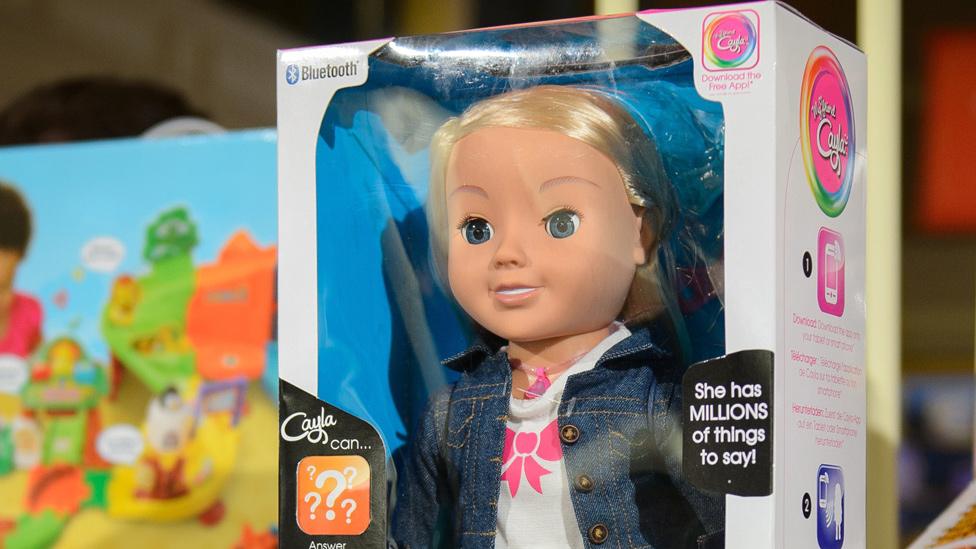
UK homes have an average of 10 smart devices, including toys such as internet-connected My Friend Cayla
The UK government has announced guidelines to make internet-connected devices safer to use following a spate of security breaches.
It includes moves to make sure passwords are unique and not resettable to a factory default and that sensitive data transmitted via apps is encrypted.
But the guidelines are not binding, leading some to question how effective they will be.
One expert said they would not stop "irresponsible" manufacturers.
As well as the stricter guidance on passwords and recommended encryption, the government's Security by Design review suggested:
Device manufacturers have a point of contact so that security researchers can report issues immediately
Software should be updated automatically with clear guidance for customers
It should be easy for consumers to delete personal data
Installation and maintenance should be easy for consumers
The government estimates that every household in the UK owns at least 10 internet-connected devices - a figure that is expected to rise to 15 by 2020.
In Germany there is a ban on the sale of smartwatches aimed at children, and the internet-connected doll My Friend Cayla over fears that both could act as spying devices.
'Fast and loose'
Ken Munro, an analyst at security firm Pen Test Partners, said of the review: "It's a good start but misses too much to be of great use."
He said: "Responsible IoT (internet of things) manufacturers are already addressing security. It's the irresponsible manufacturers who aren't interested, don't care about our security or who refuse security on grounds of cost that we need to worry about.
"Without 'teeth', this standard is meaningless. Manufacturers who already play fast and loose with our security to make a quick buck from us won't change anything."
Mr Munro also revealed that the measures suggested would not have prevented many of the recently reported security breaches of smart devices, such as the Mirai botnet that used internet-connected devices - such as CCTV cameras and printers - to attack popular websites.
In response, a spokesperson for the National Cyber Security Centre, which worked on the code of practice, said: "The Mirai botnet malware is one of many attacks that would be better defended against by following our new guidance, such as automatic updates and setting unique default passwords.
"By implementing vulnerability disclosure policies, manufacturers will also improve identification and resolution of issues, allowing consumers to receive timely updates that protect their privacy and security against new threats."
Margot James, minister for digital and the creative industries, said: "We want everyone to benefit from the huge potential of internet-connected devices, and it is important they are safe and have a positive impact on people's lives.
"We have worked alongside industry to develop a tough new set of rules so strong security measures are built into everyday technology from the moment it is developed."

Analysis: By Rory Cellan-Jones, technology correspondent
From internet-connected dolls that can be taught to swear to webcams that can be hacked and enlisted in a botnet, the dangers of this new world where everything is online are becoming evident.
What is not so clear is whether this new voluntary code of practice will make any difference.
The key word is voluntary. The kind of manufacturers who will sign up to a code are probably pretty responsible already but there are plenty of others whose only aim is to pile their insecure products high and sell them cheap.
The new policy will work only if online retailers refuse to stock products that do not comply with the code - yet DCMS (Department for Digital, Culture, Media and Sport) cannot even say whether Amazon is involved in this initiative.
Still, the consumer group Which? has backed the code as a good first step, pleased that there is at least an effort to define what makes a good secure product.
Now there will be pressure to give it some teeth by amending consumer protection laws to deal with this new threat to our security.
- Published17 February 2017
- Published2 February 2018
