Ship hack 'risks chaos in English Channel'
- Published

The English Channel is the busiest shipping route in the world
A commonly used ship-tracking technology can be hacked to spoof the size and location of boats in order to trigger other vessels' collision alarms, a researcher has discovered.
Ken Munro has suggested that the vulnerability could be exploited to block the English Channel.
Other experts suggest the consequences would be less serious.
But they have backed a call for ship owners to protect their vessels against the threat.
Mr Munro's company, Pen Test Partners, has made limited details of the hack public to coincide with London's Infosecurity Europe exhibition, where he is showing off his work.
"There are really basic steps that can be taken to prevent this from happening," he told the BBC.
"In our experience, security on board ships is often dire."
Shipping shut-down
The attack targets a computer-powered navigation system called the Electronic Chart Display (Ecdis), which provides crews an alternative to using paper charts.

Ecdis screens are found on the bridges of most modern ships
A French researcher, who goes by the nickname x0rz, had earlier demonstrated that many ships never changed their satellite communications equipment's default username and password, and that it was relatively easy to find cases via an app to gain remote access.
Mr Munro has shown that it is possible to take advantage of this to reconfigure a ship's Ecdis software in order to mis-identify the location of its GPS (global positioning system) receiver.
The receiver's location can be moved by only about 300m (984ft), but he said that was enough to force an accident.
"That doesn't sound like much, but in poor visibility it's the difference between crashing and not crashing," he said.
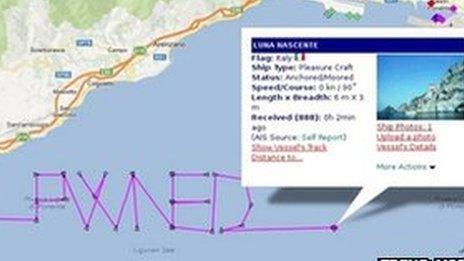
He added that it was also possible to make the software identify the boat as being much bigger than its true size - up to 1km sq.

Mr Munro took this photo of passwords recently spotted on one ship
Although the deception would be obvious to others on that scale, Mr Munro suggested it could still cause chaos.
"Ecdis feeds the automatic identification system (AIS) transceiver on many new ships," he said.
"So, AIS collision alarms would be firing on numerous ships and many would then simply avoid the area completely.
"It would make for a very brave captain to continue on course while the alert was sounding."
The consequence, he added, was a hacker could effectively shut down the Channel's shipping lanes.
Spurious results
Experts at the University of Plymouth's Maritime Cyber Threats research group have reviewed some of the details Mr Munro has shared.
"There are no technical inaccuracies in anything [Mr Munro] has said, but the cascading of effects that would be necessary to reach the worst case conclusion are extremely unlikely in practice," said Prof Kevin Jones.
His colleague Dr Tim Crichton added that the Channel Navigation Information Service - a body that monitors the flow of traffic in the area - would soon intervene if AIS collision warnings contradicted both radar readings and what deck officers could see with their own eyes.
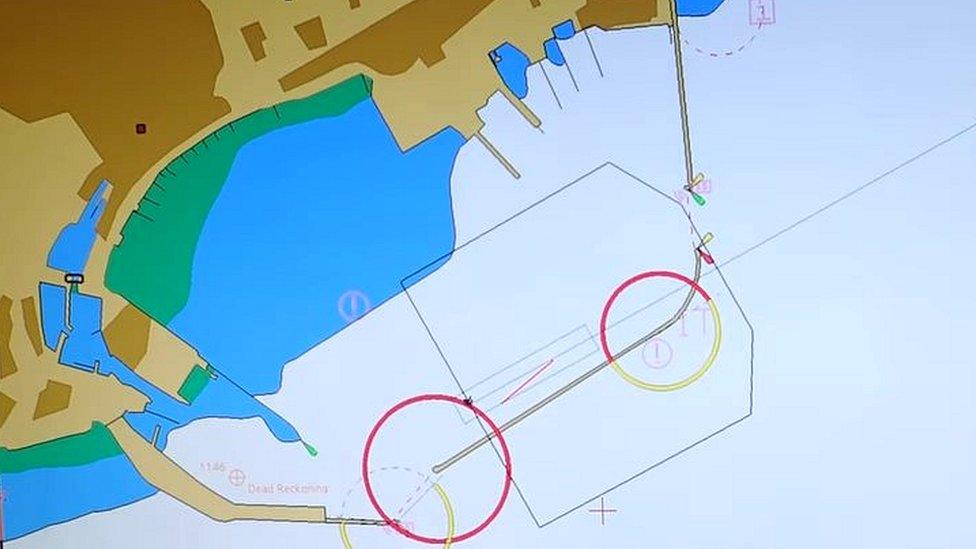
Vessels can be made to appear much larger than their true size, as denoted by the grey shape on the bottom-right of this example
"Fairly quickly, if AIS were giving spurious results in that area, an information message to all ships would be put out," he said.
Even so, another member of the department said, Mr Munro's research should not be ignored.
"Even if the vulnerabilities aren't taken advantage of in the way Mr Munro mentioned, there are probably many other ways they could be," said Dr Kimberley Tam.
Hackers could still cause damage and disruption, she said, even if shutting down the Channel completely was unlikely.
"We may not be able to secure all the systems, because they just weren't designed with cyber-security in mind," she said.
"So, instead of investing too much money in creating a technical solution that might not work, it may be easier to address human training."
'Be vigilant'
Mr Munro concurs, saying ship officers must be instructed to lock down their equipment with strong passwords and ensure the latest software patches are installed.
A spokesman for the UK's National Cyber Security Centre (NCSC) noted that it had published a best practice guide last year, external that could also prove useful.

A collision alarm could prove a distraction to ships already dealing with difficult conditions
"We are vigilant to cyber-threats wherever they come from and are ready to defend against them, but the UK government can't do this alone," said a spokesman.
"Businesses and organisations must play their part.
"By raising their basic defences, organisations of every size can protect their operating capabilities, finances and reputation, significantly reducing the return on investment for attackers."
- Published18 August 2017

- Published31 October 2013