US warns of supply chain cyber-attacks
- Published

Installing compromised software can have expensive repercussions
The US intelligence community has issued a new warning about cyber-espionage risks posed by attacks made via the technology supply chain.
A report said China, Russia and Iran were the most capable and active states involved in such economic subterfuge.
Software supply chain infiltration had already threatened critical infrastructure, it warned, and was poised to imperil other sectors.
It added that sensitive data owned by US bodies had been put at risk.
The Foreign Economic Espionage Report was published by the US's National Counterintelligence and Security Center (NCSC).
It said that last year marked a "watershed", with seven significant software supply chain events having been made public.
By comparison, only four such incidents had been widely reported between 2014 and 2016, it said.
'Key threat'
The concern is that attackers are looking for new ways to exploit computer networks via the privileged access given to technology providers.
"Software supply chain infiltration is one of the key threats that corporations need to pay attention to, particularly how software vulnerabilities are exploited," William Evanina, the NCSC's director and the US's top counter-intelligence official, told the BBC.
"To get around increasingly hardened corporate perimeters, cyber-actors are targeting supply chains.
"The impacts to proprietary data, trade secrets, and national security are profound."
The report highlights a number of attacks.
They include the spread of a booby-trapped version of CCleaner - a computer-cleaning program - which was revealed last September.
This worked by inserting malicious code into the software to take advantage of the access it enjoyed.
Millions of machines were infected, but the report said hackers had "specifically targeted" 18 companies to conduct espionage including Samsung, Asus, Intel, VMware, O2 and Fujitsu.
Lost millions
The attacks can also have disruptive effects as well as being used to steal information.
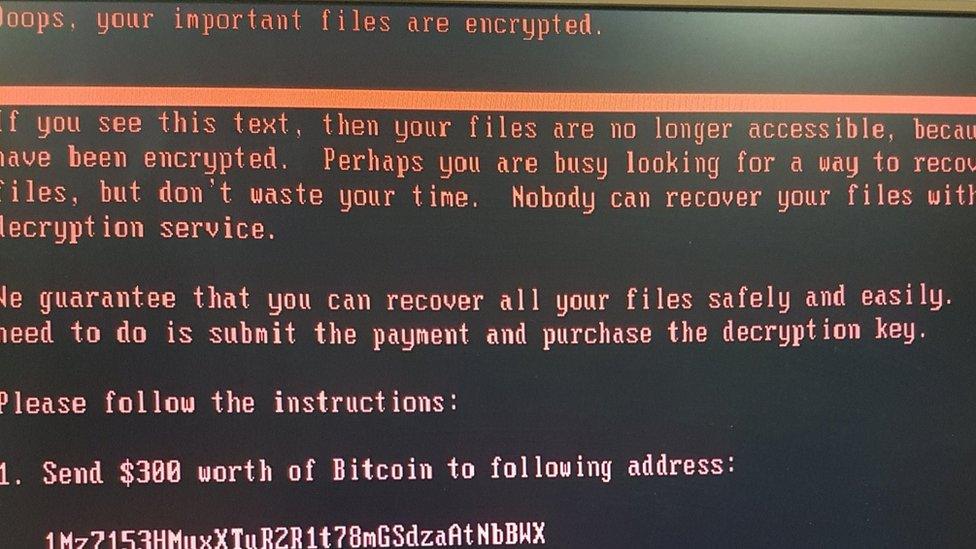
The use of accountancy software to target Ukraine in the so-called NotPetya attack is another example of where a software supply chain was compromised.
The software was used to file tax returns in Ukraine.
The NotPetya malware spread by piggybacking a tax software update
Hackers - alleged to be from Russia - implanted malicious code that wiped machines of data. It spread well beyond Ukraine via many companies that did business in the country, leading to hundreds of millions of dollars of damages.
Supply chain attacks have the potential to hit many different machines through one single compromise and can be harder to detect than traditional malware attacks.
Backdoor breaches
Another flagged case involved software from South Korean based firm Netsarang, which had been corrupted with a backdoor. This was in turn used to target hundreds of companies in the energy, financial services, manufacturing, telecoms, transport and pharmaceutical sectors.
Kingslayer was also discussed., external The malware operation targeted administrator accounts to install backdoors that provided access to sensitive parts of a target's network.
The report said that while it was not known how many firms were ultimately infected, "at least one US defence contractor was targeted and compromised".
In the past week, cyber-security company Crowdstrike also published the results of a survey it had commissioned., external Two-thirds of the organisations that responded said they had experienced a software supply chain attack in the past 12 months.
The average cost of an attack was more than $1.1m (£838,000).
Kaspersky Lab
The US report also raised concerns about foreign technology companies with close links to their domestic governments. It pointed to new laws and regulations in Russia and China, which require reviews of source code.
"New foreign laws and increased risks posed by foreign technology companies due to their ties to host governments, may present US companies with previously unforeseen threats," the report said.
It also noted last September's Department of Homeland Security directive telling US federal agencies and departments to remove Kaspersky Lab products because of the company's link to Russia.
Kaspersky Lab software has broad and privileged access to machines to scan for viruses, but the company has always denied any use of this access for espionage on behalf of the Russian state.
- Published15 June 2018

- Published15 February 2018
- Published18 September 2017
