Home car charger owners urged to install updates
- Published
WATCH: Security flaws found in home electric car chargers
Security researchers have discovered failings in two home electric car chargers.
The researchers were able to make the chargers switch on or off, remove the owner's access, and show how a hacker could get into a user's home network.
Most of the faults have now been fixed but owners are being told to update their apps and chargers, to be safe.
It comes as proposed new legislation on cyber-security for appliances - including chargers - is published.

Thousands of Project EV chargers have been sold in the UK, with buyers eligible for government subsidies
Two home chargers, Wallbox and Project EV - both approved for sale in the UK by the Department for Transport - were found to be lacking adequate security when used with an accompanying app for smartphones.
Cyber-security researcher at Pen Test Partners, Vangelis Stykas, discovered the vulnerabilities.
"On Wallbox you could take full control of the charger, you could gain full access and remove the usual owner's access on the charger. You could stop them from charging their own vehicles, and provide free charging to an attacker's vehicle.
"Project EV had a really bad implementation on their back end. Their authentication where it existed was pretty primitive, so an attacker could easily escalate themselves to being an administrator and change the firmware of all the chargers."
Mr Stykas says changing the firmware - the programming that is built in to the hardware - would allow an attacker to permanently disable the charger, or use it to attack other chargers or servers.

Security researcher Vangelis Stykas found that hackers could take full control of the charger
Pen Test Partners is one of a fast-growing number of companies in the UK that specialises in penetration testing, something commonly referred to as 'white-hat hacking.'
'White hats' aim to find security problems and report them to the companies concerned, so vulnerabilities can be corrected before hackers can take advantage of the failing.
Mr Stykas believes anyone with a little knowledge of these cloud-based web application systems could have performed the same hack.
"It's pretty obvious for anyone who can understand cloud systems and cloud communication, and it didn't take that much to spot the vulnerability and find a way to exploit it."
Home Network Access
Researchers also found it would be possible in cases where the chargers were connected by wi-fi to the home network, for hackers to also gain access.
Pen Test Partner's Ken Munro says: "Once you're on to someone's home network, if you haven't changed that router admin password, you can send all the traffic to the hacker.
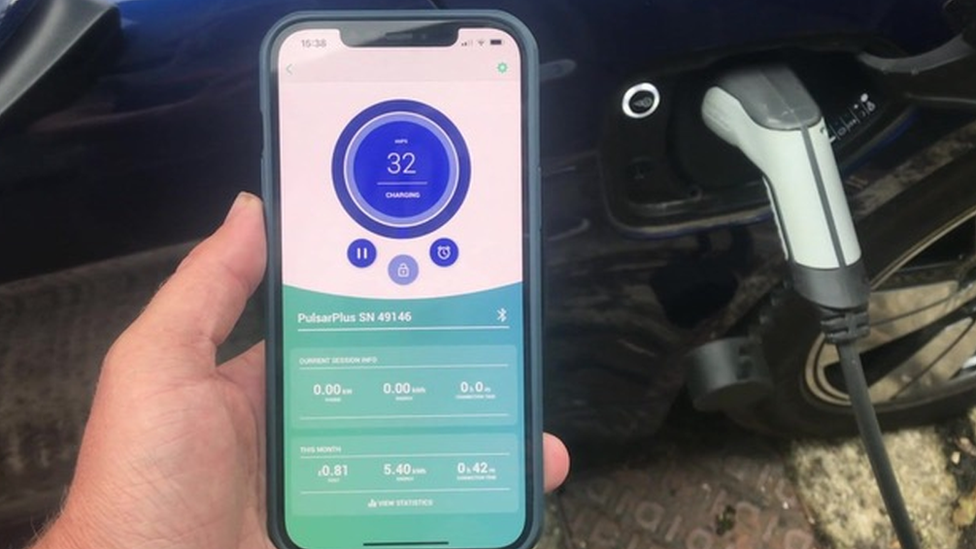
The chargers are vulnerable because they are used in conjunction with a phone app
"That means they can do things like set up sites that look like the real deal but steal your passwords and then your real bank account for example has been compromised. There's all sorts of things you can do .. so everything you do online is potentially exposed."
In its report, external into the security failures, Pen Test Partners adds that multiple chargers could be controlled at the same time using some of the vulnerabilities it found, which could potentially be used by an attacker to overload the electricity grid in some areas and cause blackouts.
Government approved
Ensuring cyber-security is part of the government's conditions for chargers to be sold in the UK, which allows buyers to receive government subsidies when making a purchase.
Thousands of units of both the Wallbox and the Project EV chargers have been sold in the UK, where eligible EV owners can get hundreds of pounds in government subsidies to help them purchase home car chargers.
fThe Department for Transport declined to comment on the two chargers found to have security flaws.
A government spokesperson told the BBC: "This autumn we will be introducing new legislation designed to further protect consumers and the energy system by mandating a range of cyber-security requirements for EV chargepoints."
In addition, the Department for Digital, Culture, Media and Sport plans to introduce similar security-focused legislation that will apply to many connected or smart consumer devices.
Flaws fixed
Both Pen Test Partners and BBC Click contacted the firms to give them the chance to fix the problems before publishing the security flaws.
Project EV, which imports chargers from a company based in China called Atess, said: "We had some speedy conversations with the manufacturer.. to improve the security of their platform.
"All the security issues raised have been addressed, with a new server, app updates and firmware updates to the chargers that are online."

Issues remained with the hardware associated with the Wallbox charger, said researchers
Wallbox, based in Spain, did not reply to the BBC in time for publication, but told Pen Test Partners they had fixed the online problems.
Re-testing suggests the web-based security problems with both chargers have been fixed. Owners are being encouraged to check for any security updates issued by the two companies.
However, Ken Munro says the Wallbox charger uses hardware - a Raspberry Pi module - that isn't secure enough.
"There's really nothing you can do to make it completely secure, so unless Wallbox have found a way of fixing that - which would be beyond me - I'd suggest perhaps supergluing the box cover in, so hackers can't take the top off."
Subsequent to the publication of this report, Wallbox contacted the BBC with a statement.
"The systems accessed by these chargers have been updated to address the software problems highlighted in this article and no further action is required by the end user," it said.
It said it uses "a Raspberry Pi Compute Model 3 for our consumer chargers", which it added "is the foundation of many consumer electronic devices".
The Raspberry Pi Foundation recommends that the module, external is not used for new designs and is currently not listed for industrial use.
The organisation later clarified that the Compute Module 3 (CM3) could continue to be used by many existing industrial partners and would receive technical support, but it added that the newer CM4 hardware, in production since 2019, offers better security features and would be supported for a longer timeframe.
Related topics
- Published6 May 2021

- Published31 December 2020
