North Korea refuses to deny Sony Pictures cyber-attack
- Published

The attack has been a major headache for Sony Pictures chairman Michael Lynton
North Korea has refused to deny involvement in a cyber-attack on Sony Pictures that came ahead of the release of a film about leader Kim Jong-un.
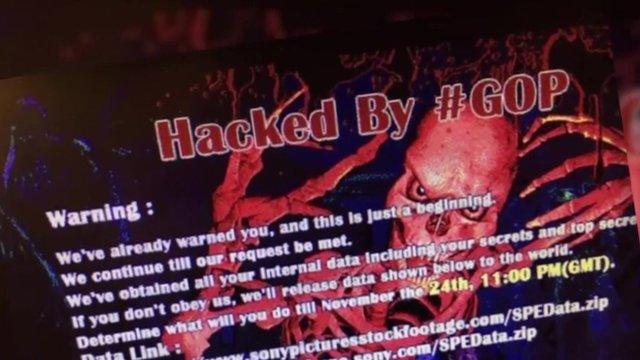
Sony is investigating after its computers were attacked and unreleased films made available on the internet.
When asked if it was involved in the attack a spokesman for the North Korean government replied: "Wait and see."
In June, North Korea complained to the United Nations and the US over the comedy film The Interview.
In the movie, Seth Rogen and James Franco play two reporters who are granted an audience with Kim Jong-un. The CIA then enlists the pair to assassinate him.
North Korea described the film as an act of war and an "undisguised sponsoring of terrorism", and called on the US and the UN to block it.
California-based Sony Pictures' computer system went down last week and hackers then published a number of as-yet unreleased films on online download sites.
Among the titles is a remake of the classic film Annie, which is not due for release until 19 December.
Alastair Leithead says North Korea is furious about the new film
The film about North Korea does not appear to have been leaked.
When asked about the cyber-attack, a spokesman for North Korea's UN mission said: "The hostile forces are relating everything to the DPRK (North Korea). I kindly advise you to just wait and see."
On Monday, Sony Pictures said it had restored a number of important services that had to be shut down after the attack.
It said it was working closely with law enforcement officials to investigate the matter but made no mention of North Korea.
The FBI has confirmed that it is investigating. It has also warned other US businesses that unknown hackers have launched a cyber-attack with destructive malware.

Analysis: Leo Kelion, technology desk editor
Suggestions North Korea could be behind the Sony Pictures hack has drawn incredulity from some, surprised that the "Hermit Kingdom" might be able to pull off such a stunt.
In fact, experts say Pyongyang's cyber-skills should not be underestimated. One US government adviser warned last year that North Korean hackers posed, external "an important 'wild card' threat" to US and international security.
Being sure about how far its cyber-capabilities extend isn't easy. A report by Hewlett Packard's security division, external noted that most North Koreans were restricted to an intranet system, separate from the wider internet, which limits their links to the outside world.
But the report noted that the state's education system places special emphasis on mathematics, which has helped it develop skilled programmers, cryptographers and security researchers.
According to a report by Al-Jazeera, external, North Korean defectors have spoken of promising students going on a two-year accelerated university course before heading to China and Russia for a year to hone their hacking skills.
A US analyst quoted a defector, external who claimed to be part of North Korea's Unit 121 hacking squad until he escaped in 2004. He said some operations had been carried out from a Pyongyang-owned hotel in Shenyang, China.
According to HP, North Korea's "cyber-warriors" are thought to have carried out a wide variety of attacks, including:
Spreading malware via video games
Stealing details of foreign technologies stored on computers
Carrying out distributed denial of service attacks (DDoS), which knock services offline by flooding them with traffic sent from hijacked foreign computers
Cyber-psychological operations - posting propaganda to social networks and "trolling" message boards
However, hacking a major corporation to make threatening demands is not a behaviour that has been linked to North Korea in the past, and the hashtag #GOP (Guardians of Peace) - used in the Sony attack - is not known to have been used by Pyongyang.
- Published2 December 2014

- Published1 December 2014

- Published6 November 2014

- Published25 November 2014

- Published26 November 2014
- Published25 November 2014

- Published25 May 2011

- Published27 April 2011
- Published27 April 2011