How the Dutch foiled Russian 'cyber-attack' on OPCW
- Published

A team of Russians allegedly tried to compromise and disrupt computers at the OPCW (file photo)
Four Russians, a car full of electronic equipment, and a foiled plot to hack the world's foremost chemical weapons watchdog.
The Dutch security services say Russia planned a cyber-attack on the Organisation for the Prevention of Chemical Weapons (OPCW) in The Hague earlier this year.
At a press conference on Thursday, Defence Minister Ank Bijleveld said the plan was thwarted with the help of officials from the UK.
Russia has described the allegations as a "diabolical cocktail" and a "rich fantasy".
Here is what we know about the alleged plot so far.
The suspects

The four suspects travelled on diplomatic passports
Dutch and British officials have named four Russians they say are agents in a GRU intelligence cyber warfare team.
Specifically, GRU's Unit 26165, which has also been known as APT 28 and has been accused of conducting cyber operations around the world.
Alexei Morenets, 41, and Yevgeny Serebriakov, 37, were described by officials as "cyber-operators".
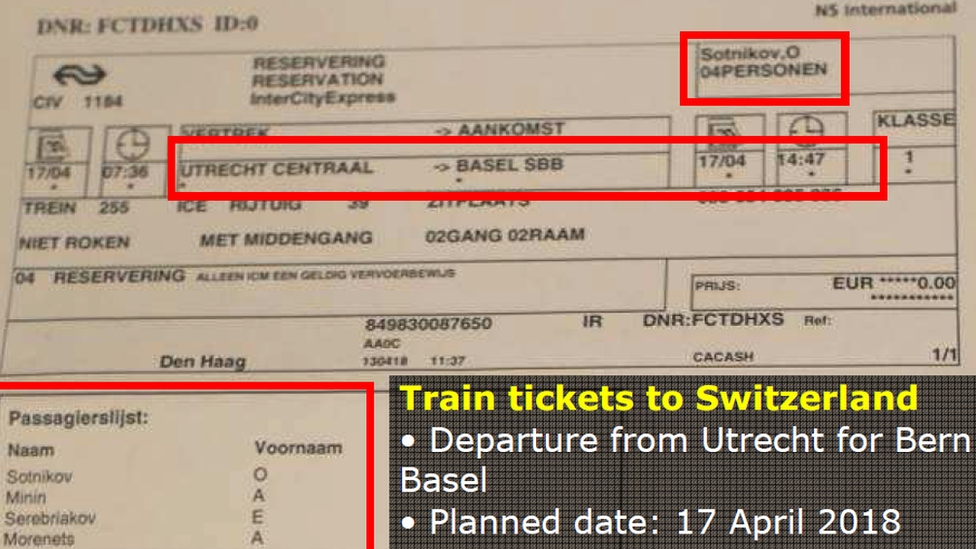
Oleg Sotnikov and Alexei Minin - both aged 46 - were also named as support agents.
They allegedly travelled to the Netherlands on diplomatic passports and arrived in the country on April 10.
"They were clearly not here on holiday," the head of the Dutch intelligence service said on Thursday.
Yevgeny Serebriakov's laptop was ultimately seized by the authorities, and his search history showed he had researched the OPCW building and its surroundings.
It also included a picture of him at the Olympic games in Brazil in 2016 alongside an unidentified Russian athlete.

Yevgeny Serebriakov pictured at the Olympic Games in 2016
The target
The OPCW has been investigating the poisoning of Russian ex-spy Sergei Skripal and his daughter in the UK.
Authorities believe Mr Skripal's door in the city of Salisbury was targeted with the nerve agent Novichok.
The organisation was also examining an alleged chemical attack by Syria's Russian-backed military in Douma.
The OPCW is the world's top chemical weapons watchdog, and in June granted itself new powers to assign blame for attacks despite protests by Russia.
At the time, Russia said the organisation was going beyond its mandate and Industry Minister Georgy Kalamonov said it was like a "sinking ship".
The plot
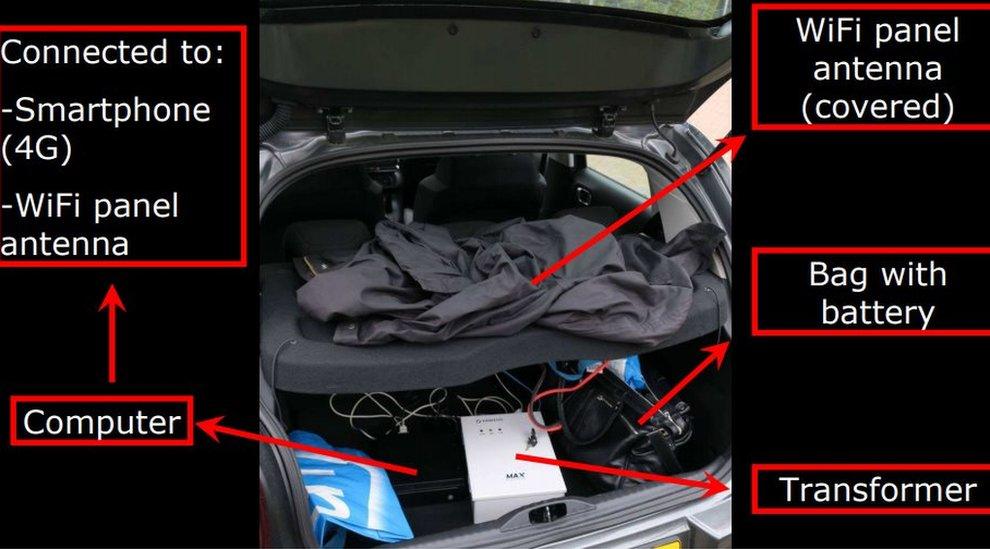
After arriving in the country, the team of Russians hired a grey Citroen C3 car and were seen scouting the area around the OPCW building.
Alexei Minin's recovered camera shows a number of reconnaissance photographs of the area which were taken on 11 April.
All the while the group were being closely monitored by the Dutch intelligence service.
They planned to carry out a closed access hack operation targeting the OPCW's wifi network, officials say.
In the rear of the car they had set up specialist equipment for doing this, and parked the vehicle in the car park of a nearby Marriot hotel.
The equipment included an antenna which was hidden under a waterproof jacket and aimed at the OPCW office. This was being used to intercept login details, Maj Gen Onno Eichelsheim from the Dutch MIVD intelligence service said.
The goal was to compromise and disrupt computers in the building, officials say.
They then planned to travel to Switzerland on 17 April, as shown by train tickets that were in their possession, but they were intercepted before they could leave.


A well-known technique
Mark Ward, technology correspondent
Close or "drive-by" attacks on wi-fi networks are well known in the cyber-security world. They are an established technique for penetrating a target.
They work well because some wi-fi hotspots can harbour hardware weaknesses that can be exploited to grab traffic. Some run third-party software that can contain vulnerabilities.
There have also been instances of hotspot makers picking passcodes that are easy to generate. And researchers have demonstrated fundamental weaknesses in the protocols used to create hardened passcodes.
Then there are the issues with the way wi-fi works, which make it possible to force gadgets that use wireless to hop onto fake, copycat networks. All of this would be well known to the average nation-state-backed hacker.

The response
The group were being continually monitored by the intelligence services, and were eventually intercepted by the authorities on 13 April.
When this happened they tried to destroy one of the mobile phones they were carrying, which officials say shows their heightened awareness of security.
They had also collected their litter from the hotel they were staying at, also allegedly for security reasons.
The four men were detained and expelled to Moscow rather than being arrested. This is probably because they had diplomatic passports and, under the 1961 Vienna Convention, diplomats are theoretically immune from prosecution.
They were escorted to Schiphol airport and put on a plane without any of their items, and the intelligence services were in charge of the operation.
"The decision taken at the time of catching the operatives was to disrupt as quickly as possible so we deported them, it was not a police operation," the director of the Dutch intelligence service said.
The evidence
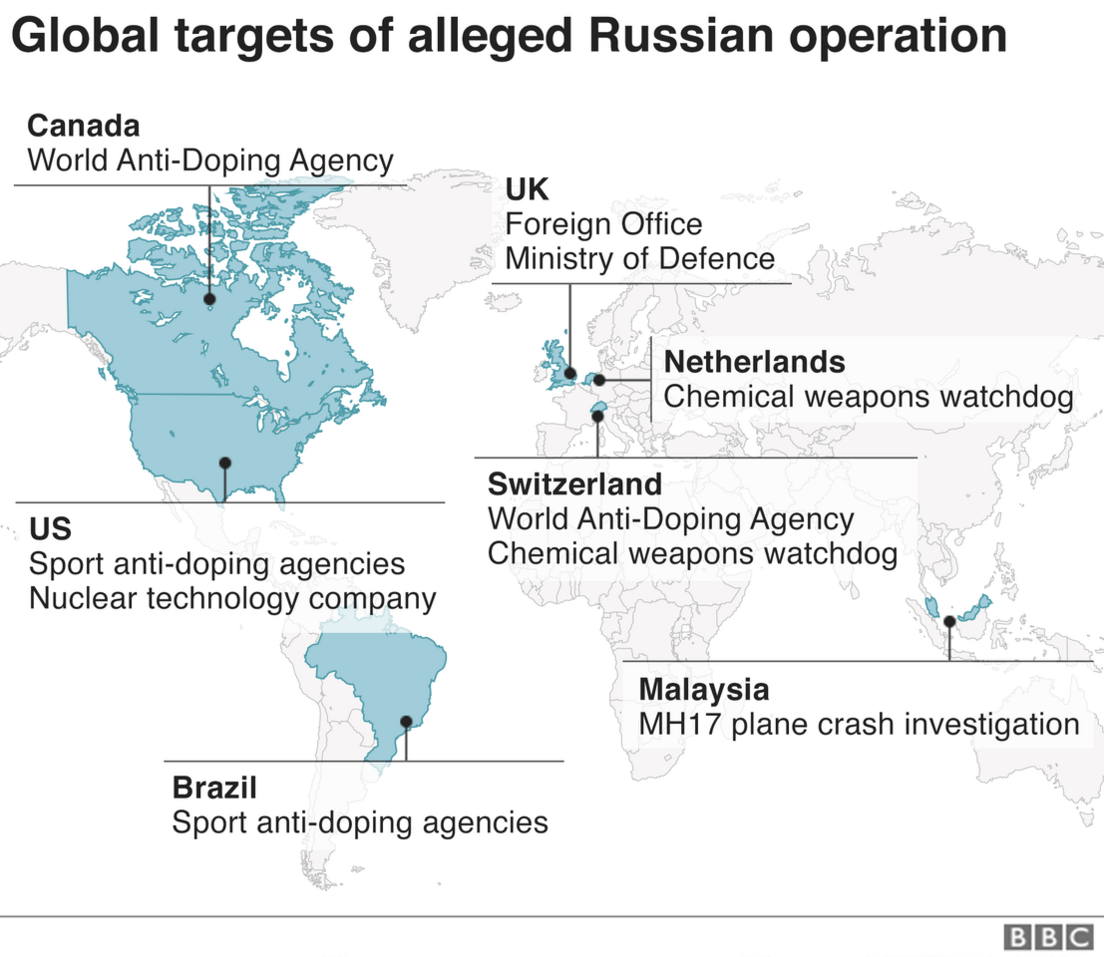
As well as the specialist equipment in the car, Yevgeny Serebriakov's laptop was found to have been used in Brazil, Switzerland and Malaysia.
In Malaysia it was used to target the investigation into the downing of Malaysia Airlines flight MH-17 over rebel-held territory in eastern Ukraine in 2014, killing all 298 people on board.
Earlier this year Dutch-led international investigators concluded that the missile belonged to a Russian brigade. Russia has denied any involvement in the plane's destruction.
Separate data from the laptop showed it was also present in the Swiss city of Lausanne where it was linked to the hacking of a laptop belonging to the World Anti-Doping Agency (Wada), which has exposed the taking of performance-enhancing drugs by Russian athletes.
Officials also found Alexei Morenets's taxi receipt, which showed he had travelled from the GRU headquarters to a Moscow airport on 10 April - the day they arrived in the Netherlands.
There were also a number of print-outs from Google Maps showing Russian diplomatic buildings in Switzerland, where they had planned to travel.
- Published4 October 2018

- Published16 April 2018
- Published27 September 2018

- Published4 October 2018
