Will quantum computers disrupt critical infrastructure?

Many organisations are developing quantum computers
- Published
Twenty five years ago computer programmers were racing to fix the millennium bug amidst fears that it would cause banking systems to crash and planes to fall out of the sky.
Much to everyone's relief the impact turned out to be minimal.
Today, some fear there is a new critical threat to the world’s digital infrastructure. But this time, we cannot predict exactly when it will move from theory to reality, while the ubiquity of digital technology means fixing the problem is even more complicated.
That’s because the arrival of quantum computing means that many of the encryption algorithms that underpin and secure our hyperconnected world will be trivially easy to crack.
Quantum computing is radically different to the “classical” computing used today. Instead of processing binary bits which exist in one of two states – one or zero, on or off – quantum computing uses qubits, which can exist in multiple states, or superpositions.
“The reason why it's so powerful is because you're doing all those possible computations simultaneously,” Prof Nishanth Sastry, director of research for computer science at the University of Surrey, explains. This means it's “much, much more efficient, much, much more powerful.”
This means quantum systems offer the possibility of solving key problems that are beyond classical computers, is areas such as medical research and materials science, or cracking particularly complex mathematical problems.
The problem is some of those same mathematical problems underpin the encryption algorithms that help to ensure trust, confidentiality and privacy across today’s computer networks.
Today’s computers would take thousands, even millions of years, to crack current encryption standards, such as RSA. A suitably powerful quantum computer could, theoretically, do the job in minutes.
This has implications for everything from electronic payments and ecommerce to satellite communications. “Anything that's protected by something that's vulnerable becomes fair game for people that have access to quantum relevant computers,” says Jon France, chief information security officer at non-profit cybersecurity organization ISC2.
Quantum computers capable of breaking asymmetric encryption are thought to be years away.
But progress is being made.
In December, Google said its new quantum chip incorporates key "breakthroughs" and "paves the way to a useful, large-scale quantum computer".
Some estimates say a quantum device capable of breaking current encryption would require 10,000 qubits, while others say millions would be needed. Today’s systems have a few hundred at most.
But businesses and governments face a problem right now, as attackers could harvest encrypted information and decrypt it later when they do gain access to suitably powerful devices.
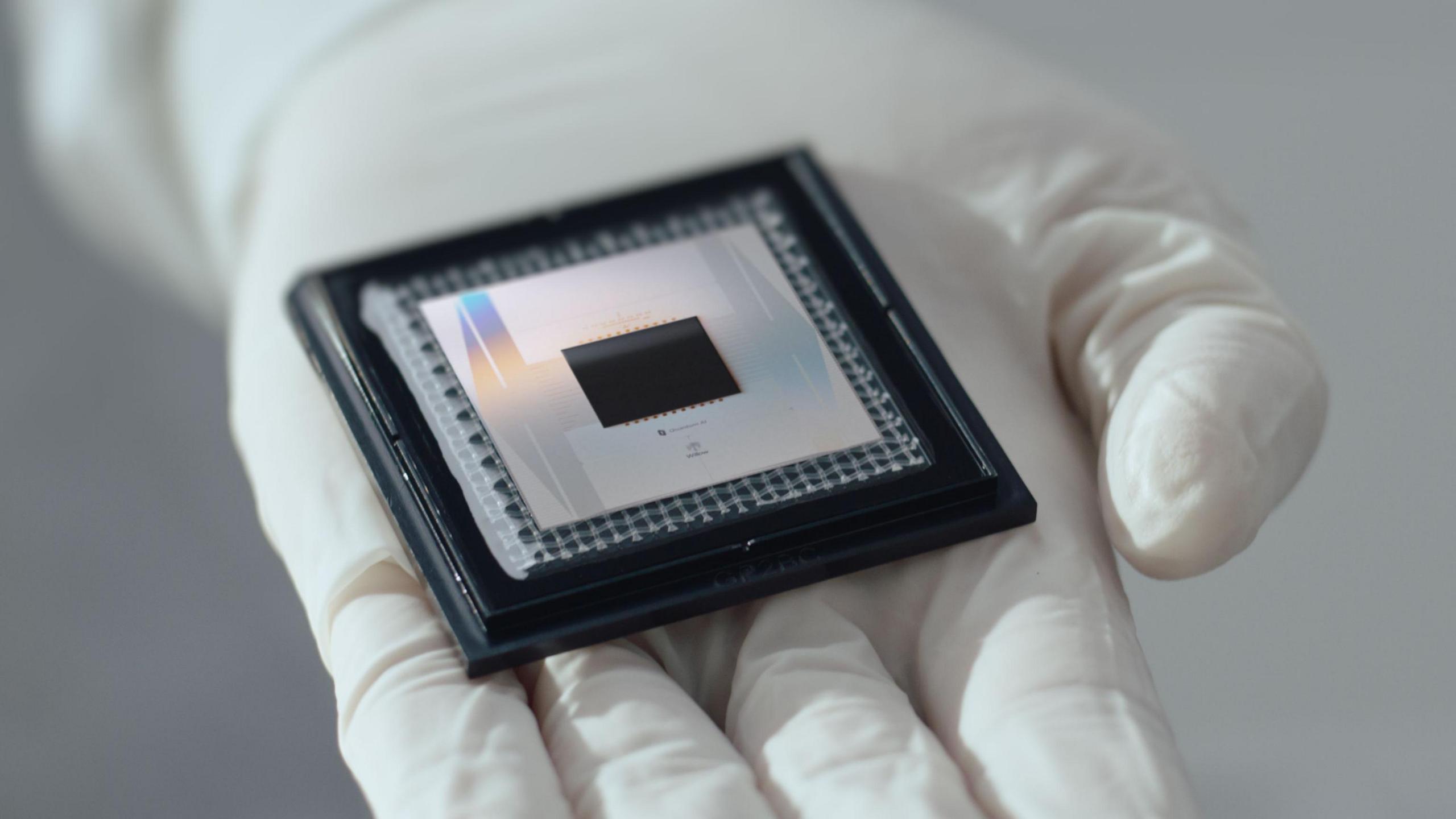
Google's says its new computer chip brings useful quantum computers closer
Greg Wetmore, vice president for software development at security firm Entrust, says if such devices could emerge in the next decade, technology leaders need to ask, “What data in your organization is valuable for that period of time?”
That could be national security information, personal data, strategic plans, and intellectual property and secrets - think of a soft drink company’s “secret” formula or the precise balance of herbs and spices in a fast food recipe.
Mr France adds, if quantum computing becomes widespread, the threat becomes more immediate with the encryption that protects our daily banking transactions, for example, potentially trivial to break.
The good news is that researchers and the technology industry have been working on solutions to the problem. In August, the National Institute of Standards and Technology in the US released three post quantum encryption standards.
The agency said these would “secure a wide range of electronic information, from confidential email messages to e-commerce transactions that propel the modern economy.” It is encouraging computer system administrators to transition to the new standards as soon as possible, and said a further 18 algorithms are being evaluated as backup standards.

Critical infrastructure like water treatment plants will need security upgrades
The problem is this means a massive upgrade process touching virtually all our technology infrastructure.
“If you think about the number of things out there with asymmetric encryption in them, it's billions of things. We're facing a really big change problem,” says Mr France.
Some digital infrastructure will be relatively easy to upgrade. Your browser, for example, will simply receive an update from the vendor says Mr France. “The challenge really comes in discrete devices and the internet of things (IOT),” he continues.
These might be hard to track down, and geographically inaccessible. Some equipment – legacy devices in critical national infrastructure such as water systems, for example – might not be powerful enough to handle the new encryption standards.
Mr Wetmore says the industry has managed encryption transitions in the past, but “It's the sharper discontinuity that makes this threat more serious.”
So, it is trying to help customers build “crypto agility” by setting out policies now and using automation to identify and manage their cryptographic assets. “That's the secret to making this transition an orderly one and not a chaotic one.”
And the challenge extends into space. Prof Sastry says many satellites – such as the Starlink network – should be relatively straightforward to upgrade, even if it means briefly taking an individual device offline temporarily.
“At any given point in time, especially with the LEO (low earth orbit) satellites, you've got 10 to 20 satellites above your head,” Prof Sastry says. “So, if one can't serve you, well so what? There are nine others that can serve you.”
More challenging, he says, are “remote sensing” satellites, which include those used for geographical or intelligence purposes. These carry a lot more compute power on board and typically include some sort of secure computing module. A hardware upgrade effectively means replacing the whole device. However, says Prof Sastry, this is now less of a problem thanks to more frequent and lower cost satellite launches.
While the impact of the millennium bug might have been minimal in the first days of 2000, that's because an immense amount of work had gone into fixing it ahead of a known deadline, says François Dupressoir, associate professor in cryptography at the University of Bristol.
By contrast, he adds, that it is not possible to predict when current encryption will become vulnerable.
"With cryptography," says Mr Dupressoir "If somebody breaks your system, you will only know once they've got your data."
Technology of Business
- Published17 February

- Published14 February
- Published24 January
