Facebook removes 'foreign interference' operations from Iran and Russia
- Published
Facebook said both operations acted "on behalf of a government or foreign actor"
Facebook has removed two separate networks of fake accounts originating in Iran and Russia, for "engaging in foreign or government interference".
The Russian operation, which Facebook linked to the country's military intelligence services, focused primarily on Ukraine and neighbouring countries.
The small Iranian operation used accounts and personas on Facebook and Instagram to post content about US politics and the 2020 presidential election.
Both operations attempted to directly contact politicians, public figures and journalists, a tactic used by several other information operations in the past.
Nathaniel Gleicher, head of Facebook's security policy, said in a blog post, external that both operations were removed for violating the company's "coordinated inauthentic behaviour" policy, not their content.
The social network defines the policy as "when groups of pages or people work together to mislead others about who they are or what they are doing", external.
'Intelligence operation'
The Russian network used dozens of fake personas to post pro-Kremlin and anti-Western messages on Facebook, Twitter, blogs and news websites.
It focused primarily on Ukraine, but some of Russia's neighbouring countries, such as Moldova, the Baltic states and Turkey, were also targeted. A few accounts also focused on Germany and the UK, but "left little trace of online activity", according to Graphika, external, a social media analytics firm.
The messaging pushed by the network echoed some of the key Kremlin media talking points, including attacks on the White Helmets volunteers in Syria and pro-Western politicians in Ukraine, as well as talk of perceived Russophobia in the West.

With the 2020 US election approaching, Facebook is under pressure to curb the spread of disinformation on its platforms
In total, 78 Facebook accounts, 11 pages, 29 groups and four Instagram accounts have been removed. Much of their activity goes back to 2016-2018, but some of the accounts were still active at the time of the takedown.
According to Graphika, blogs formed "the backbone" of the network, with operators using fake accounts on Facebook and Twitter to target selected audiences with long-form blog posts.
Mr Gleicher explained that some of the fake accounts posed as citizen journalists and "tried to contact policymakers, journalists and other public figures".
"The operators picked their targets with care, and took pains to create realistic-looking accounts, many of which had unique profile pictures, rather than images copied from elsewhere online," Graphika said.
But at least one of the targeted individuals denies ever being in touch with the fake accounts.
Eskender Bariev, a member of a Crimean Tatar governing body which opposes the Crimea annexation, was allegedly "entrapped" by a fake account posing as a journalist into making divisive comments in a Facebook correspondence.
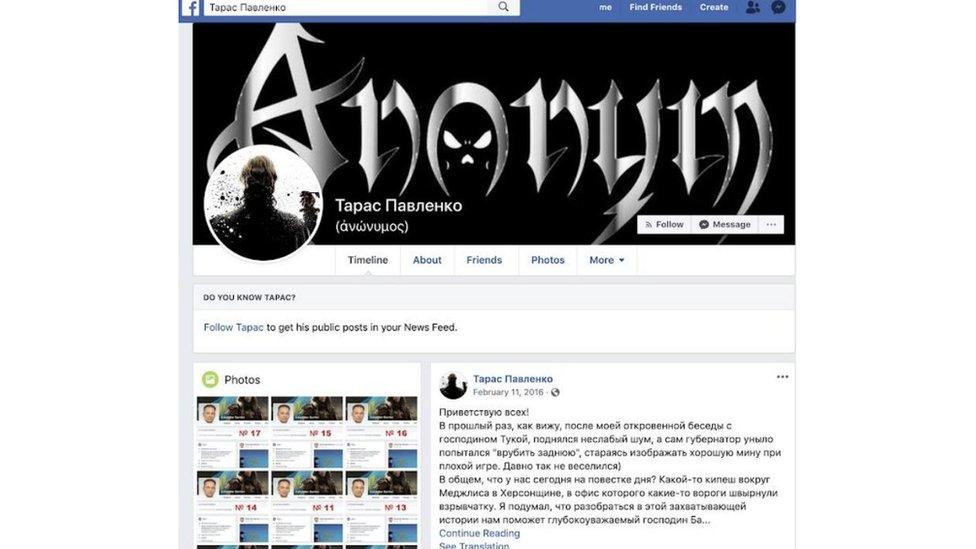
This Russian account posed as a journalist at the US-funded Radio Free Europe/Radio Liberty
But Mr Bariev himself told Radio Liberty's Krym.Realii website that he had had "no correspondence in the said period of time", external and that his responses to questions differed from his usual style.
Ben Nimmo, director of investigations at Graphika, told the BBC that the Russian network's "overall reach was very limited", but their operators still managed "to plant some of their stories on genuine news sites in Ukraine and Moldova".
"It's a classic approach for an intelligence operation: establish a false persona, then poison the well of information," he added in a tweet, external.

You may also be interested in:

'Continuity'
The Iranian operation was much smaller, in terms of size and scale. Consisting of six Facebook and five Instagram accounts, the network only managed to gain 60 followers on Instagram.
Facebook said it was able to spot the network, as it demonstrated links to a much larger operation originating from Iran which it had taken down last year, external.
FireEye, a US cyber-security firm which was given prior access to some of the content posted by the network, said in a blog post that personas in the network posed as US liberals, external and amplified content "directly in line with Iranian political interests".
The firm also spotted a network of under 40 accounts on Twitter, which in some cases showed "direct overlap" with the accounts on Facebook and Instagram.
In one case, a persona using the name "Ryan Jensen" posted the same video of an anti-war protest to Instagram and Twitter following the US assassination of Iran's top general Qasem Soleimani.
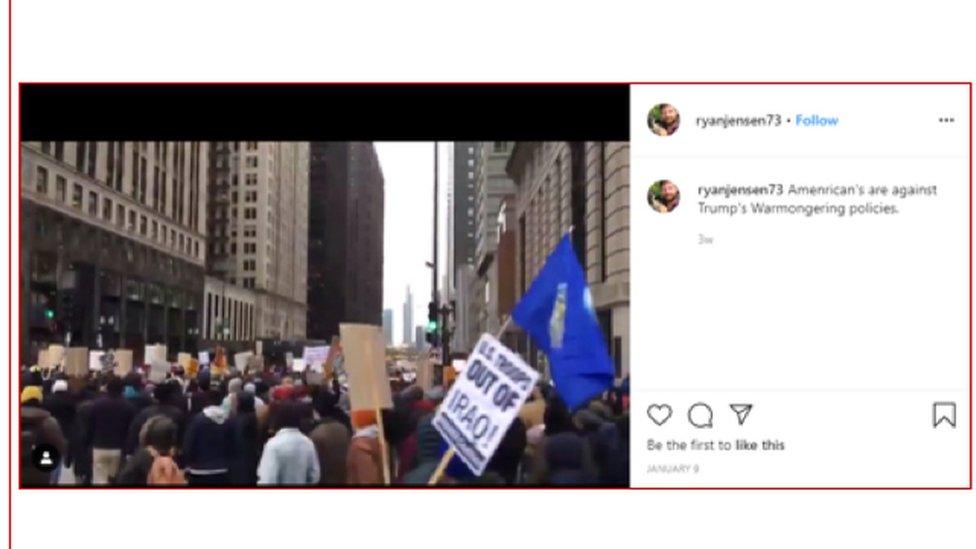
This US anti-war protest video was posted after the killing of Iran's top general Qasem Soleimani
The accounts on Twitter constantly replied to tweets by members of the US Congress, journalists and media outlets, often using the same hashtags.
The personas were notable for their poor use of English, and also the fact a simple search would reveal that none of them were journalists or media personalities.
"This was not a new type of activity, but it shows continuity in terms of the narrative and using commentary from authentic figures," Lee Foster, information operations intelligence analyst at FireEye, told the BBC.
"It's not surprising that this was a small operation. If you are pretending to be journalists soliciting interviews from public figures, you probably don't need hundreds of accounts."
Much like the Russian operation, the accounts "picked their targets individually and engaged them personally", Mr Nimmo said.
"There's much more to online disinformation and propaganda efforts than trolling and fake media reports. Politicians and journalists need to be aware that they're targets, and be wary."
- Published30 January 2020

- Published14 September 2019

- Published30 May 2019

- Published22 January 2018
