If 2017 could be described as 'cyber-geddon', what will 2018 bring?
- Published

Scenarios once the province of thriller writers are now anything but fiction in the world of cyber-security. That is the lesson of the past year.
It's a process one British official describes as "Hollywoodisation". And if 2017 was notable for the escalation and the proliferation of cyber-attacks, it's left everyone asking what will happen in 2018?
The so-called WannaCry attack in May was perhaps the best example.
The idea that we could see hackers - perhaps linked to Russia - steal code from America's National Security Agency, publish it, and then have North Korean hackers repurpose it before using it to take down a significant part of Britain's National Health Service, would previously have been dismissed as fantasy.
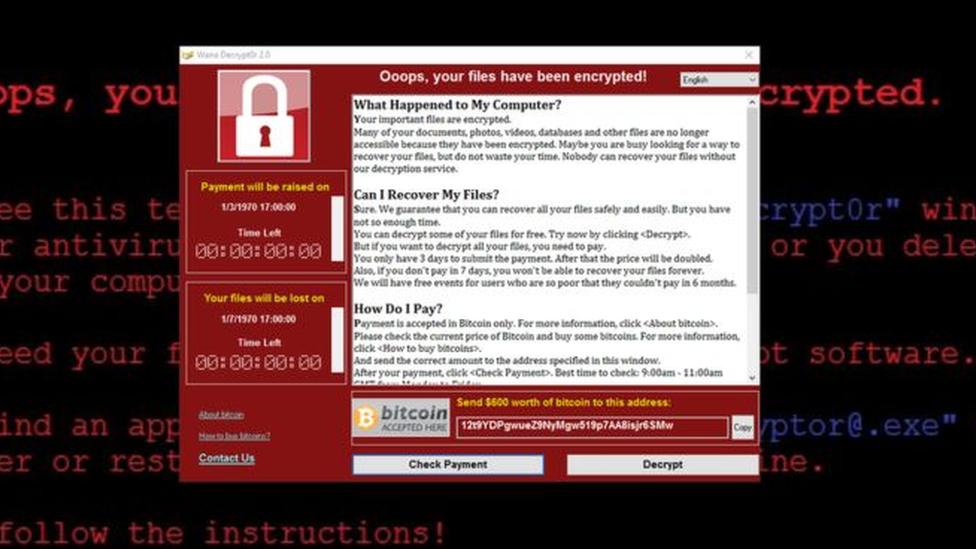
WannaCry spread to more than 150 countries in a worldwide attack
And yet that is exactly what many people think happened.
The best guess is in this case, the attack was actually a money-making scheme gone wrong, which spread far faster than expected.
But it showed how ransomware - locking a machine - could be used as a weapon, and just how vulnerable many parts of our society are to this threat.
The fear for the future is that more high-end attack tools could be stolen, shared and made use of.
The other high-profile attack came the following month.
Widely dubbed "NotPetya", it hijacked the update service of a Ukrainian tax software firm that had to be used by everyone doing business in the country, and then spread through the company's networks, again locking computers with ransomware.
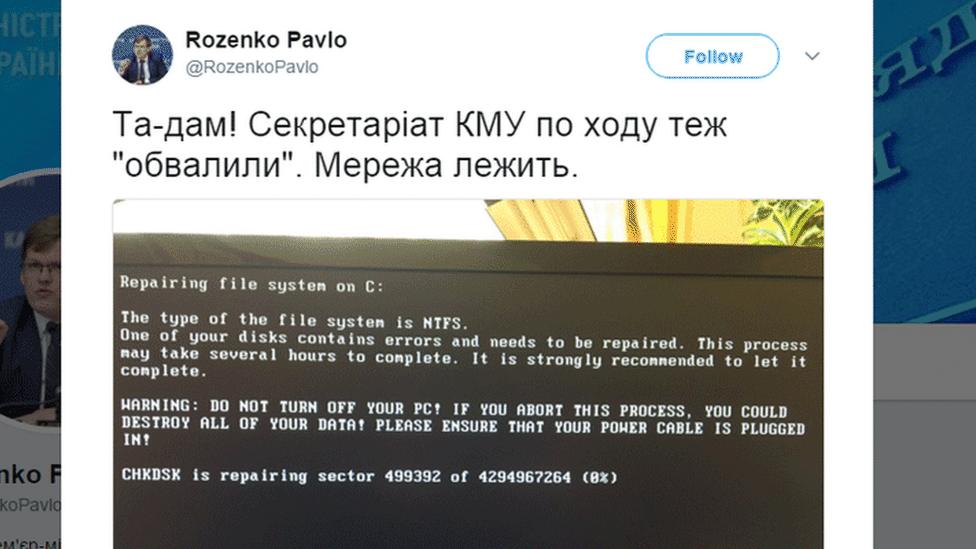
Ukraine's deputy prime minister tweeted a photo appearing to show government systems being affected, with the caption "Ta-daaa!"
The aim here was to disrupt, rather than make money, since the key to decrypt the files was not even accessible.
"This was fake crime," says Sean Kanuck, a former US official now with the International Institute for Strategic Studies.
Real-world consequences
It soon became clear that any company with a subsidiary or an office linked to Ukraine could be hit, and the attack spread far and wide, with estimates of corporate losses running into the hundreds of millions of dollars.
This was widely interpreted as a Russian attack, and only the latest on Ukraine, after hackers had previously taken a power station offline.
"They have this ransomware facade, which allows them to say, 'This is criminal and nothing to do with us,'" says John Hultquist of the cyber-security company FireEye.
He's been watching Russian activity for over a decade, and has been surprised by what he has seen recently.
"I would never have expected them to have gone so far," he says.

National Cyber Security Centre chief executive Ciaran Martin warned that Russia had targeted British energy, telecoms and media
Suddenly states are carrying out cyber-attacks with destructive, real-world consequences.
It is clear that there is a willingness to escalate and push the boundaries in cyber-attacks.
And no-one has quite worked out yet where this will stop.
In November, the head of Britain's National Cyber Security Centre, Ciaran Martin, warned that Russia had targeted British energy, telecoms and media sectors.
Other breaches have also upped the stakes.
The theft of data belonging to about 150 million people from the company Equifax was less novel than other attacks but still significant - partly because it revealed just how much personal data could be held by one company without the public ever really understanding how it got there.

Former Equifax boss Richard Smith testified before US Congress about the breach
Sean Kanuck also points to the hacking of America's Security and Exchange Commission as another major event, because of the possibility of using information for insider trading and market manipulation.
Proliferation of capability
It raises serious questions about the integrity of the financial system.
Chinese cyber-intrusions against the US dipped after a deal done by the Obama administration - although an attack against technology service providers called Cloud Hopper and linked to China was under-reported, given the way it was able to leverage access into many other companies.
But other countries have become more visible - a sign of proliferation of capability.
Threat-intelligence companies say they have seen more activity by Iran in particular, and warn that it may be the country to watch.
It was blamed for a hack of the British Parliament this year, which briefly took systems off-line, and there are concerns it too could turn to destructive attacks.
Geopolitics ties in closely to cyber-behaviour.
Worsening tensions with North Korea could lead to it unleashing more activity.

Relations between North Korea and the international community have soured over its nuclear programme
"The financial sector - particularly stock markets, major companies - and energy infrastructure is where it will try and strike back if possible," says Cameron Colquhoun, of Neon Century intelligence. "It's a classic asymmetric response."
The deteriorating regional situation in the Middle East and the potential end of the Iran nuclear deal could also lead Tehran to do more, and analysts have seen Iranian-linked actors exploring critical infrastructure.
FireEye says it has seen increased activity recently from two different hacking groups linked to Iran (known as APT 33 and 34) with possible reconnaissance of finance, energy and telecoms sectors.
'Weaponise information'
More generally, a number of countries in the Middle East, including Qatar, the United Arab Emirates and Saudi Arabia, may well be more willing to engage in different levels of cyber-attack as they build up their capability.
The use of cyber-hacking for political interference has also been a significant development.

Former FBI director Robert Mueller is investigating Russian interference in the 2016 US election
Information was hacked from the US Democratic Party and Hillary Clinton officials in 2016, but the scandal has only grown since.
And the Macron campaign in France saw similar activity in 2017.
In her Mansion House speech in November, British Prime Minister Theresa May also warned that Russia was "seeking to weaponise information", although so far the evidence for Russian interference in the UK is more limited, and Russia has denied all the allegations about interference and cyber-hacking.
And in December Foreign Secretary Boris Johnson and his Russian counterpart Sergei Lavrov clashed in Moscow over alleged Russian cyber attacks against Western countries.
Russia "tries to sow discord in the West"
The issue of political interference has also marked a shift in understanding that cyber is not just about cyber.
In the case of America, information from the DNC - the Democratic party's governing body - was hacked and then disseminated through a range of channels and pushed across social media.
In other words, the hacking element was only one part of a larger operation.
Approaching cyber-security narrowly risks missing the extent to which Russia in particular has integrated it into a wider range of activities, which often go under the rubric of "hybrid warfare".
This is part of a wider trend to use information as a weapon. And it is not just states.
Infrastructure at risk
Companies and non-state actors are increasingly seeking to steal data and release it or shape information flows to suit their agendas (or sometimes just to make money by moving markets).
The issue here is manipulating the flow of information, of which "cyber-security" is only one aspect.
So what next?
The fear is that the trend of escalating destructive attacks - and a proliferation of those able to carry them out - spells trouble.
In particular, there may be greater targeting of critical infrastructure.
Could cyber-attacks cause major disruption, as a catastrophic BA power failure did in May?
In the past, much of this has been pre-positioning of malicious code so that an attack could be carried out in the future, but now we may start to see things such as telecoms, airports and power stations, turned off.
Cyber-attacks are becoming part of foreign policy and defence, and are increasingly being used aggressively and not just discussed in abstract or in the realms of hypothetical scenarios.
With no sign of agreed norms on what is - or is not - acceptable behaviour in cyber-space, get ready for some more surprises in the year ahead.
- Published19 December 2017

- Published15 November 2017

- Published14 November 2017

- Published31 October 2017

- Published27 October 2017

- Published8 September 2017

- Published28 June 2017

- Published13 May 2017
- Published30 March 2016
