Swann's home security camera recordings could be hijacked
- Published

Swann's cameras are sold at high street stores as well as online
A popular wireless security camera designed to safeguard businesses and homes was vulnerable to a spying hack.
The flaw meant it was possible to hijack video and audio streamed from other people's properties by making a minor tweak to Swann Security's app.
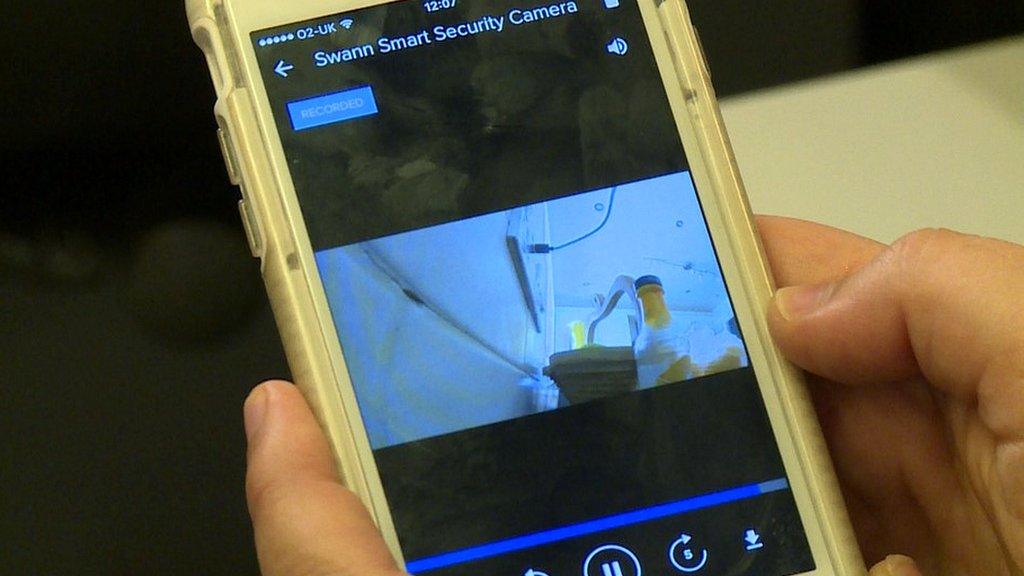
Researchers found the problem after the BBC reported a case where one customer had received another's recordings.
Australia-based Swann and OzVision - the Israeli provider of its cloud tech - said the issue had now been fixed.
Swann said that the vulnerability had been limited to one model - the SWWHD-Intcam, also known as the Swann Smart Security Camera - which first went on sale in October 2017. Retailers including Maplin, Currys, Debenhams, Walmart and Amazon have sold them.
However, there are concerns that other companies' cameras supported by OzVision could have problems.
The discovery has left the man whose kitchen was inadvertently shown to another Swann camera owner feeling unhappy.
The West Midlands-based IT worker, who asked the BBC to refer only to his first name, contacted the broadcaster after it published the original article four weeks ago.
Watch: Video footage from a family's kitchen was leaked via Swann's app
At the time, Swann had described the problem as a "one-off".
"It's a gross breach of privacy - I wouldn't buy another product from them," Harry said, adding that he owned five of the affected cameras.
"I've got a four-year-old and it sends a shiver down my spine to think somebody could have been watching my family.
"It's quite a scary thought."
Open access
Five Europe-based security consultants teamed up to investigate Swann's cameras after the June report: Ken Munro, Andrew Tierney, Vangelis Stykas, Alan Woodward and Scott Helme.
They discovered a new vulnerability - that free software tools commonly used within the cyber-security industry could be used to intercept messages sent from OzVision's computer servers to the Safe by Swann app.

Swann's cameras are "weatherproof" and installed outside some owner's properties
Safe by Swann is used to view cameras' motion-triggered recordings via a smartphone.
The intercepted messages included a reference to a unique serial number given to each camera in the factory.
By altering the serial number, the researchers were able to obtain video feeds from other cameras - something they tested by typing in numbers belonging to other cameras that they had bought.
At no point were they required to type in the other accounts' usernames and passwords.
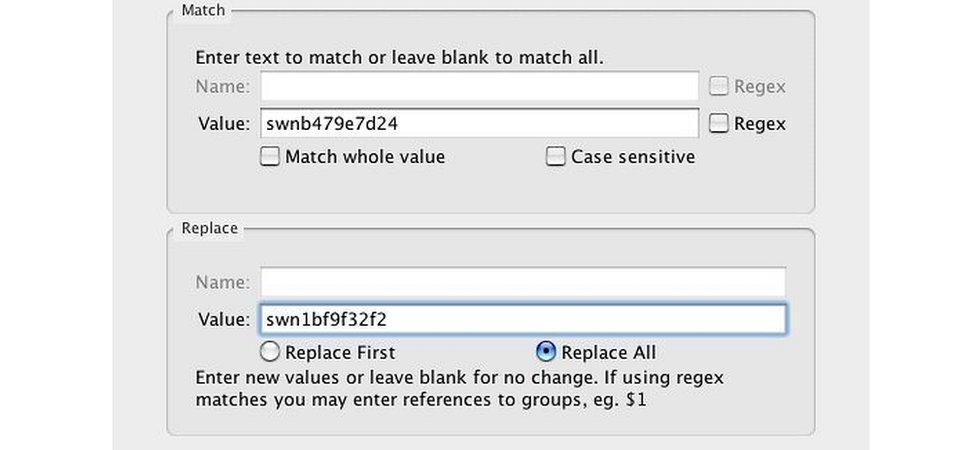
There are several programs that make it possible to substitute one serial number for another
They also found a way to identify the serial numbers Swann's cameras were using, which theoretically gave the researchers the ability to view any active account and flick between them at speed.
However, they did not view these feeds as this would have been a breach of the Computer Misuse Act.
Instead, they reported their findings to Swann, which confirmed the problem.
"Swann was able to detect the subsystem Ken Munro and his team were attempting to hack and promptly addressed the vulnerability," said a spokeswoman for the company.
"This vulnerability did not apply to any other Swann products. We have not detected any other such attempts."

The researchers sourced this feed from one of their colleague's cameras based 200 miles away
Mr Munro confirmed that the hack no longer worked.
"I'm glad that Swann has fixed the problem - but had we not found it, I have to wonder who else might be looking at people's footage now," he said.
Millions of feeds
After reporting the problem with Swann's camera, the researchers discovered that a US-based security consultancy had previously flagged, external a similar issue with another brand supported by OzVision - Flir FX.
Despite Flir having been told of this a year ago, Mr Munro's team found it was still able to hijack feeds in a similar manner to the way it had done with Swann's kit.
Two camera models were compromised as a result - the FXV101H and FXV101W.

The researchers found a way to hijack feeds from two Flir FX cameras
The cameras are now sold and maintained by Lorex Technology, a subsidiary Flir sold to China's Dahua earlier this year. It has now acknowledged the issue and published an advisory note to users, external.
"We can confirm there is a potential vulnerability with the original Flir FX cameras, which were manufactured between 13 February 2015 and 13 January 2016," it told the BBC.
"We have assessed the risk to be low but take any potential vulnerability very seriously.
"We are actively working with Flir and our technology partners to address this potential vulnerability and expect to implement the solution soon."
OzVision's website says it supports more than three million active video channels.
Its sales executive Uri Kerstein told the BBC that a "thorough security check" was under way.
"A security concern which was raised a few weeks ago was immediately addressed and resolved by the company and its partners," he said.
"OzVision is conducting a thorough examination of the system to ensure that any remaining or potential security concerns are resolved within days."

OzVision's website states it supports more than three million online video feeds
Despite this assurance, Mr Munro suggested there was a risk involved with using any internet-based security camera system.
"I'd make sure you don't put them in very personal places like your bedroom," he said.
"Just bear in mind someone might be looking in."
- Published27 June 2018