This rigged charger can hijack your new laptop
- Published
- comments
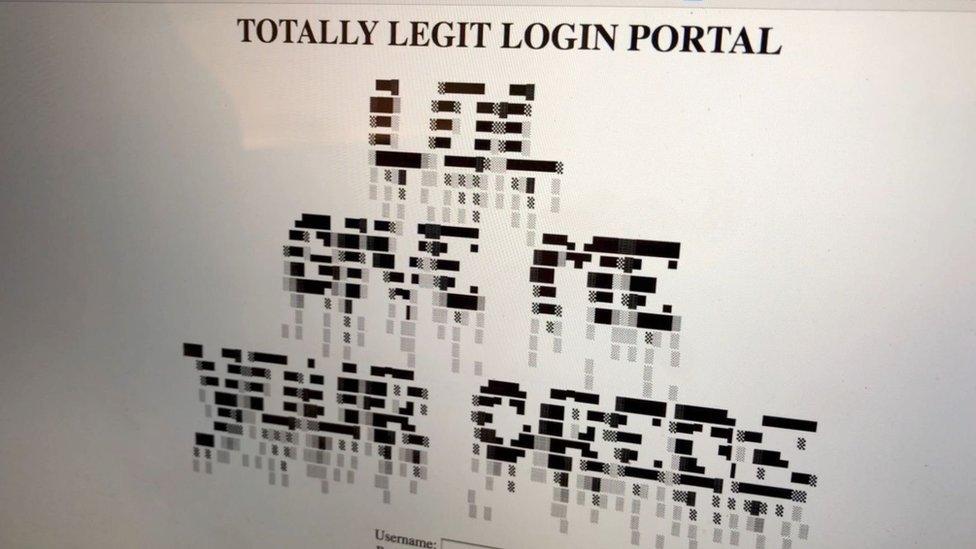
"Give me your creds" - The hijacked machine could be used to collect user data
A neat feature of many modern laptops is the ability to power them up through the USB port. Unlike the rectangular USB ports of old, the newer type - USB-C - can carry enough power to charge your machine.
That’s great news: it means you don’t need to add a separate port just for charging. And when the USB port isn’t being used for power, it can be used for something useful, like plugging in a hard drive, or your phone.
But while you and I may look at that as an improvement, hackers see an opportunity to exploit a new vulnerability.
One researcher, who goes by the name MG, external, showed me how a Macbook charger could be booby-trapped. Modified in such a way it was possible to hijack a user's computer, without them having any idea it was happening.
It’s the kind of hack that gives security professionals the chills. The ubiquitous white, square chargers for MacBooks are seen in the offices and coffee shops of the world. They are borrowed, lost and replaced on a regular basis.
Nasty things
MG gutted the inside of the charger and filled it with small components - that’s all he’ll say about it, on the record - that are powered up when the unsuspecting victim connects it to their computer.
It’s extremely hard to detect - it still charged the laptop as normal.

MG is keeping most of the details of the hack a secret

The hijacking device was able to insert a fake log-in screen into a website. Were he to use this technique for real, he could use this method to scoop-up whatever data I entered into the fake site.
"In the demo we're just capturing a username and password,” MG told me.
"But this can also inject malware, root kits and persistent types of infections that could be malicious.”
MG is early in the testing phase, but he predicts the attack would likely work on any machine that uses USB-C to get its power.
"In this case it’s an Apple, but it works on HP, Lenovo and a lot of others,” he said.
Apple did not reply to a request for comment, nor did the USB Implementors Forum, the group responsible for supporting the standard.
Charing desperation
I met MG in a hallway at Def Con, an annual conference for hackers held in Las Vegas. Typically, researchers use the event to explain, in mind-frying detail, how a vulnerability works - a process that comes well after informing the manufacturer and giving them a chance to fix it.
But in this case, MG is keeping the precise details to himself. He doesn’t work for a security company, and so he is inviting other researchers to work with him to see how this technique could be used, but said he may make his findings public eventually.
The attack in principle is not a new discovery. In mobile phones, where the charging point is often the same slot through which the device sends and receives data, hackers have already been known to carry out so-called “juice jacking” attacks, external. These prey on a person’s desperation to get some much-needed charge.
What is different is that deployment of this kind of attack on computers, made possible since the move to USB-C.
“These types of attack are not new,” explained David Rogers, from security consultancy Copper Horse, and also a lecturer at Oxford.
“Users need to exercise good hygiene when it comes to plugging anything into their machines or phones and avoid using public charging stations.
"Equally, equipment makers using USB for both charging and data need to adopt a security-by-default approach which means designing devices so that they automatically only use charge mode, rather than immediately allowing data transfer.”
Not a good idea
The simplest way to protect against this kind of attack is obvious: keep an eye on your charger. But from a technical standpoint, MG said added defenses could be put in place to make the user aware of what is being plugged in - even if it could interrupt the simplicity that made USB popular.
"When you plug in a device and it's automatically trusted, that may not be a good idea,” he said.
"We could start doing some level of trust-based pairing that we see with Bluetooth devices, or some level of firewall so that at least the first time a new device is plugged in you should be alerted.”
But, as any security researcher will tell you, the weakest point in any defense is the human. And history has shown us that making unsuspecting people plug something into their computers is surprisingly easy. One of the most famous cyber-attacks, blamed on Israel and the US, though never confirmed, began with a USB flash drive being plugged into a computer at an Iranian power plant.
Many companies, including IBM, have banned employees from using USB sticks. It would much more difficult, you’d imagine, to prevent employees plugging in malicious chargers that look identical to the real deal.
________
Follow Dave Lee on Twitter @DaveLeeBBC, external
Do you have more information about this or any other technology story? You can reach Dave directly and securely through encrypted messaging app Signal on: +1 (628) 400-7370