Grindr accounts could be easily hacked with email address
- Published

A hack on Grindr allowed anyone with the email address linked to a valid account to reset the user's password and take over their profile.
Security experts revealed the vulnerability online - and reported it the LGBT dating app.
It enabled full access to an individual's account, including images, messages and HIV status.
Grindr said: "Thankfully, we believe we addressed the issue before it was exploited by any malicious parties."
The flaw was discovered by French security researcher Wassime Bouimadaghene and documented by security experts Troy Hunt and Scott Helme.
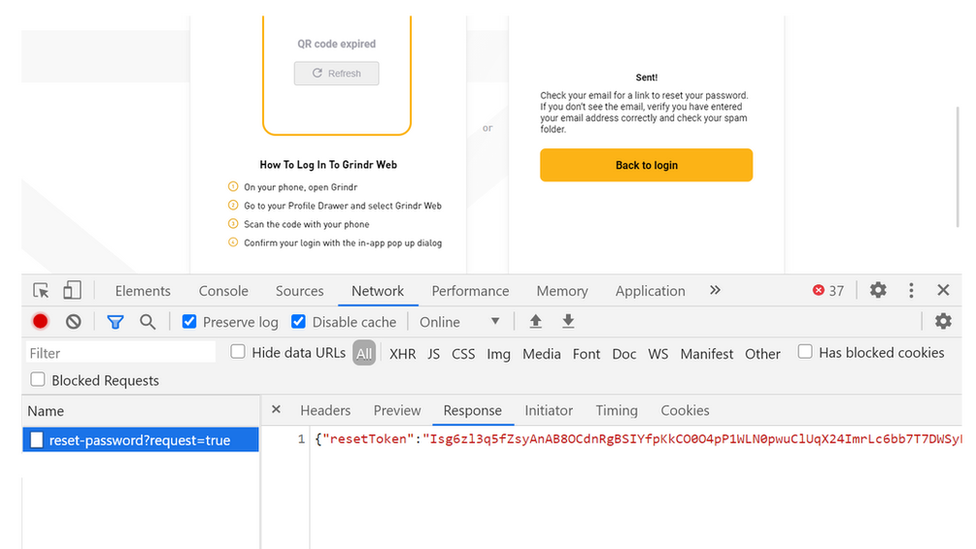
Hackers could find a reset-password link within the website's code
How it worked:
To take over an account, the hacker would enter the target's email address on Grindr's password-reset page
A link was then emailed to the owner to allow them to change their password - but that same URL could also be found in the code of the website
The hacker could then enter that URL into a new page and reset the password of the account
This enabled them to control the account and have access to the personal data stored there, including account photos, messages, sexual orientation, HIV status and last test date
Grindr chief operating officer Rick Marini told news website TechCrunch, external: "We are grateful to the researcher who identified a vulnerability.
"The reported issue has been fixed."
Grindr was working to improve reporting procedure and incentives for security researchers to flag these issues, Mr Marini added.
In 2018, the app was criticised for sharing data, including HIV status, with two external companies.
It said the information had been shared to help test and improve the app.
- Published3 April 2018
- Published2 September 2020

- Published25 March 2019
