Cyber-attack website Webstresser taken down
- Published
Site seized: The splash page that has replaced webstresser since the takedown
A website blamed for launching more than four million cyber-attacks around the world, including attempts to crash banks in the UK, has been taken down in a major international investigation.
The operation, which involved the UK's National Crime Agency, blocked Webstresser.org - which allows criminals to buy attacks on businesses.
The site was used by a British suspect to attack high street banks last year, causing hundreds of thousands of pounds of damage.
Six suspected members of the gang behind the site have been arrested, with computers seized in the UK, Holland and elsewhere.
What was the website doing?
Webstresser: Investigators say it posed as a legitimate business
The site targeted in this week's operation was one of many operating openly on the web as a "stresser" business, offering to test a company's cyber-defences.
Investigators say that the gang sold cyber-attacks for as little as $14.99 (almost £11) - meaning that anyone who wanted to attack a web service could do so with little chance of being traced.
Webstresser offered a form of cyber-attack known as Distributed Denial of Service (DDoS), in which a target website is overwhelmed by requests for access.
In practice, this means that the target, be they an online bank or a secondary school's portal for students, can seize up and crash, unless the attack is blocked.
Stresses are also used to settle scores between business rivals, carry out industrial espionage or to hold businesses to ransom.
Identifying how the attack is being launched and where it is coming from requires huge amounts of effort, as specialist online investigators must hunt for the source of the crippling data.
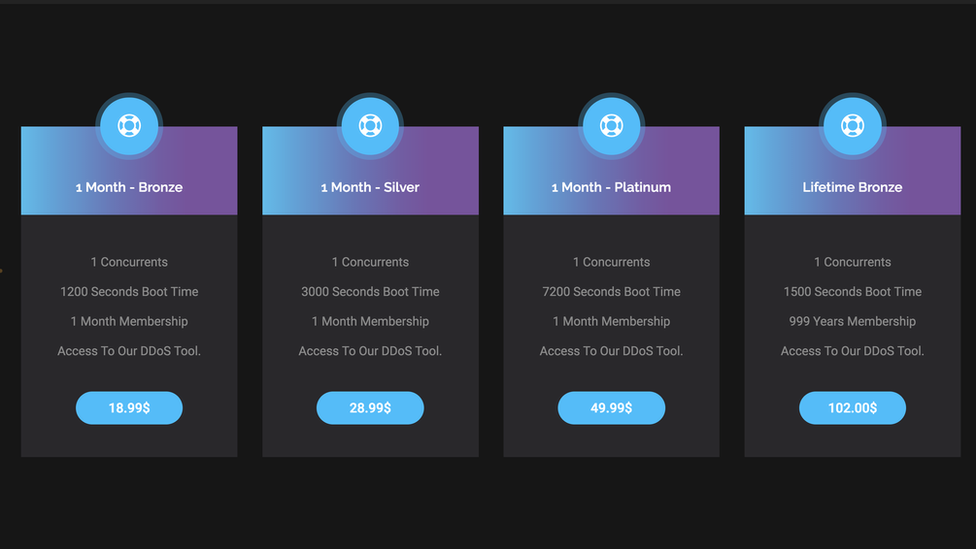
Sliding scale of costs: Clients offered different levels of service
What action has been taken ?
Over the last two days, seven suspected members of the group behind webstresser.org were arrested or subject to searches in the Netherlands, Serbia, Croatia and Canada, with support from Police Scotland, Europol and US authorities.
On Wednesday morning, Dutch police completed the operation by identifying the location of the website's servers and seizing them, replacing the site with a page announcing that law enforcement agencies had taken the service offline.
Who were the targets in the UK?
Investigators from the NCA's National Cyber Crime Unit searched an address in Bradford linked to a suspect who is believed to have used webstresser to attack seven of the UK's biggest banks in November last year.
The BBC understands that the banking attack incident, which has never been publicly confirmed, cost some of the institutions hundreds of thousands of pounds as they were forced to shut down systems while experts worked around the clock to repel the attack.
Jo Goodall, the lead investigator in the operation for the National Crime Agency, said: "Cyber-crime by default is a threat that crosses borders. The arrests made over the past two days show that the internet does not provide bulletproof anonymity to offenders and we expect to identify further suspects linked to the site in the coming weeks and months.
"We have seen how cyber-attacks have real-world consequences resulting in actual physical harm, as well as causing reputational and financial damage to businesses of all sizes."
In general, how are UK firms coping with cyber-attacks?
The UK government has just published its latest annual survey, external looking at how businesses and - for the first time - charities are handling data breaches and attacks.
The study is based on the responses of 1,519 companies and 569 charities to a telephone questionnaire carried out between October and December.
The headline findings were:
that 43% of the businesses and 19% of the charities had reported a breach or attack in the previous year
that 74% of the businesses and 53% of the charities said that cyber-security was a high priority for senior management
yet only 27% of the businesses and 21% of the charities said they had formal cyber-security policies
the average cost incurred by a breach that resulted in a financial loss was £3,100 for businesses and £1,030 for charities
the most common type of attack reported by those that had suffered a breach had involved their staff being targeted by a fraudulent emails or websites
"Given how many breaches UK businesses are facing, not training staff on why security is important invites trouble," commented Piers Wilson from cyber-security firm Huntsman.
"Just as we don't let people drive without getting their licence, every untrained employee could pose a threat."
- Published23 January 2018

- Published10 April 2018