NHS cyber-attack: Amber Rudd says lessons must be learnt
- Published
Amber Rudd: NHS trusts must learn and upgrade
The NHS "must learn" from Friday's cyber-attack and upgrade its IT systems, the home secretary has said.
Amber Rudd told the BBC the services of 45 NHS organisations in England and Scotland had been disrupted amid a global attack that affected organisations across the world.
She stressed there was no evidence patient data had been compromised.
The head of the UK's cyber-security agency said experts were "working round the clock" to restore NHS systems.
Ciaran Martin, who leads the National Cyber Security Centre - part of GCHQ - said it was doing "everything in our power" to get "vital services" back up and running.
He said that the anonymous nature of cyber-crimes means it will take time to understand how, and by whom, it was done.
The government emergency Cobra committee is meeting this afternoon to discuss the attack.
Tens of thousands of computers were injected worldwide in 99 countries on Friday, in what Europol described as an "unprecedented" attack.
The Nissan car plant in Sunderland was among global firms targeted, but the firm said there had been no major impact on its business at its site on Wearside.
French car maker Renault and telecoms giant Telefonica, which owns the O2 network, were also affected.
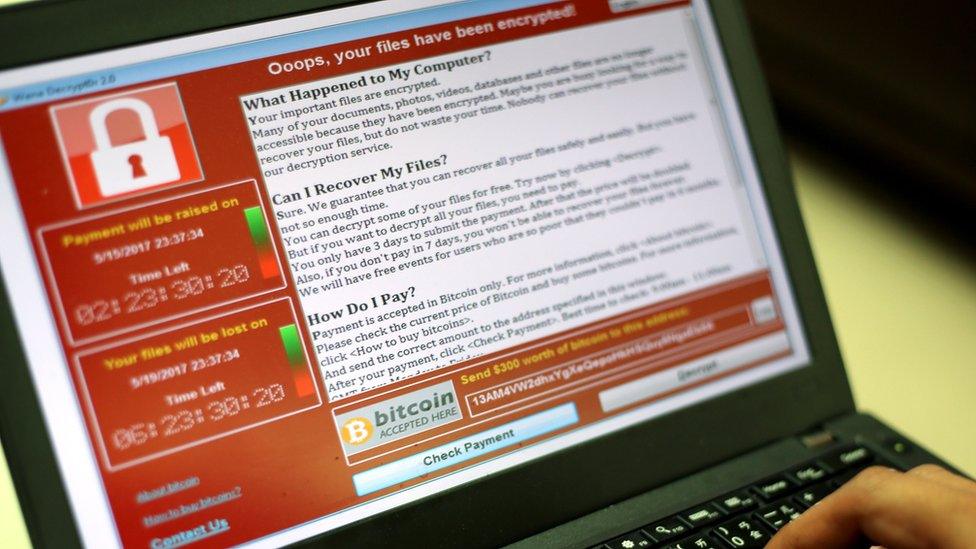
The attack on the NHS has left some hospitals and GPs unable to access patient data, after their computers were locked by a ransomware program demanding a payment worth £230.
Hospitals across the UK are cancelling operations and ambulances have been diverted from hospitals in some areas.

The issue with NHS's 'ageing' IT
The ransomeware infection has hit computers in 99 countries
Experts say one potential security issue is that many organisations still use out of date operating systems such as Windows XP.
Data obtained by software firm Citrix under Freedom of Information rules in December suggested this was the case in up to 90% of NHS trusts, but NHS Digital says it is a "much smaller number".
Ms Rudd accepted Windows XP was "not a good platform" for keeping data secure.
She told Sky News that the health secretary Jeremy Hunt had already instructed NHS trusts not to use the 2001 operating system.
"I would expect NHS trusts to learn from this and to make sure that they do upgrade," she said.
Shadow health secretary Jonathan Ashworth added that he had written to Mr Hunt, saying the public had a right to know exactly what the government would do to ensure such an attack was "never repeated again".
Responding, Ms Rudd said the government had doubled spending on cyber-security to £1.9bn between 2016 and 2021.
Brian Lord, the former director for intelligence and cyber operations at GCHQ, told BBC's Newsnight that the NHS was particularly vulnerable to such attacks because of its ageing IT systems and "complex interconnectivity".
In response to the global attack, Microsoft said it had rolled out a free security update to Windows XP, Windows 8, and Windows Server 2003 "to protect their customers".

How are patients affected?
NHS cyber attack: "My heart surgery was cancelled"
NHS England said patients needing emergency treatment on Saturday should go to A&E or access emergency services as they normally would.
But some trusts have asked people not to attend unless it is urgent.
London's Barts Health NHS Trust, the largest trust in the country, cancelled all outpatient appointments at its five hospitals on Saturday.
The NHS in Wales and Northern Ireland has not been affected.
Ms Rudd told BBC Breakfast she could not confirm all NHS files had been backed up.
"I hope the answer is yes - those are the instructions that everybody has received in the past.
"We will find out over the next few days if there are any holes in that."
She added: "There may be lessons to learn from this but the most important thing now is to disrupt the attack."

Patient's story: 'Pulled out' of MRI scan

Ron Grimshaw, 80, was halfway through an MRI scan to test for prostate cancer at Lister Hospital in Stevenage, Hertfordshire, when staff became aware of the attack.
I got there at 11am, went through the usual formalities. Got my gown on, they put a feed into my wrist to send dye around my blood stream.
I was put in the scanner for ten minutes and then I was pulled out again.
The nurses were saying something about a cyber-attack meaning their systems were down.
They weren't sure when it was going to start again so I waited for a bit. But it never happened and I went home.
I was meant to have a chest X-ray as well and that was cancelled."
I gave them my mobile number and they said they'd ring me back telling me when to come in.
You've got to sympathise with the nurses as they will have to work extra hours.
It was unbelievable you don't expect to go to hospital in the middle of a cyber-attack. Damn nuisance.

Analysis: Why do companies still use Windows XP?
Technology explained: what is ransomware?
By Chris Foxx, technology reporter
Many jobs can be done using software everyone can buy, but some businesses need programs that perform very specific jobs - so they build their own.
For example. a broadcaster might need specialist software to track satellite feeds coming into a newsroom or a hospital might need custom-built tools to analyse X-ray images.
Developing niche software can be very expensive: programming, testing, maintenance and continued development all adds up.
Then along comes a new version of Windows, and the software isn't compatible. Companies face the cost of upgrading computers and operating system licences, as well as rebuilding their software from scratch.
So, some choose to keep running the old version of Windows instead. In some businesses, that's not a huge risk, but in a hospital the stakes are higher.

How did the attack work?
Experts discuss the attack: "The most terrifying thing about this is how simple it is"
The ransomware used in the attack is called WannaCry and attacks Windows operating systems.
It encrypts files on a user's computer, blocking them from view, before demanding money, via an on-screen message, to access them again.
The virus is usually covertly installed on to computers by hiding within emails containing links, which users are tricked into opening.
Some experts say the attackers used a weakness in Microsoft systems which is known to the US National Security Agency as "EternalBlue".
A cybersecurity researcher tweeting as @malwaretechblog has claimed to have found a way to slow down the spread of the virus after registering a domain name hidden in the malware.
They said that the malware makes a request to a domain name, but if it is live the malware stops spreading.
A security update - or patch - was released by Microsoft in March to protect against the virus, but it appears many organisations have not applied the patch - or may still be using outdated systems like Windows XP.

