Snowden leaks: GCHQ 'spied on Facebook and YouTube'
- Published

The latest Snowden leaks suggest cyber-spies monitor trending videos on YouTube
YouTube video views, Facebook "likes" and Blogger visits are among activities GCHQ has monitored in real-time, according to the latest Snowden leaks.
Details of an alleged GCHQ programme codenamed Squeaky Dolphin have been published by NBC News, external.
It reports that the UK intelligence agency showed off its abilities to the US National Security Agency in 2012.
Facebook has since started encrypting its data, but Google's YouTube and Blogger services remain unencrypted.
Both firms have said that they did not give GCHQ permission to access the data.
The alleged operation's leaked logo - showing a dolphin holding a canister branded GTE - appears to refer to Global Telecoms Exploitation, a GCHQ division believed to be capable of collecting data from fibre-optic cables.
According to an earlier leak, published by the Guardian, external, GCHQ has been tapping fibre-optic cables to create a "buffer" of information it could search through since at least 2011, as part of a scheme called Tempora.
The paper said that by 2012 the agency had tapped more than 200 cables - including transatlantic communication links - and was able to process phone and internet data taken from up to 46 of them at a time.
GCHQ declined to comment on the specifics of the latest report.
However, the prime minister has previously said that: "I'm satisfied that the work these agencies do is not only vital but is properly overseen."
Real-time activity
The NBC report is based on a presentation entitled, external Psychology: A New Kind of Sigdev [signals development]. It was part of the trove of documents former NSA contractor Edward Snowden passed to journalist Glenn Greenwald, who contributed to NBC's report.
The papers refer to the use of Splunk Dashboard to provide real-time analysis of how people use YouTube, Facebook and Blogger.
Splunk is commercially available software designed to let organisations "listen" to their own data.
Examples that GCHQ is said to have shown off include:
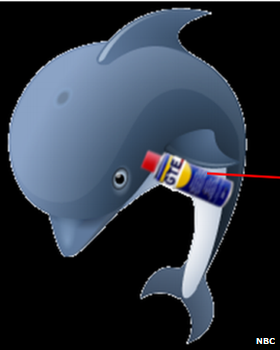
The Squeaky Dolphin logo appears to show the mammal holding a can of WD40 lubricant that has been rebranded GTE
a table showing how many people based in the city of Lagos looked at a specific job vacancies blog over a 24-hour period
a graph showing how many London-based internet users "liked" links about former Defence Secretary Liam Fox on Facebook over a week-long period
a pie chart highlighting 20 trending YouTube video tags a day before planned anti-government protests in Bahrain
Although the examples provided do not identify specific users, NBC suggests this would have been possible to do if GCHQ had access to such data.
"We have long been concerned about the possibility of this kind of snooping, which is why we have continued to extend encryption across more and more Google services and links," a spokesman for Google told the BBC.
"We do not provide any government, including the UK government, with access to our systems. These allegations underscore the urgent need for reform of government surveillance practices."

GCHQ says that its surveillance activities are carried out in accordance with UK laws
A spokesman for Facebook added: "Network security is an important part of the way we protect user information, which is why we finished moving our site traffic to HTTPS [encryption] by default last year, implemented Perfect Forward Secrecy, and continue to strengthen all aspects of our network."
Twitter also targeted
US and UK officials have stressed that while they may scoop up a lot of data, their actual use of it is targeted.
David Drummond, Google Chief Legal Officer on Edward Snowden's revelations that the NSA hacked Google data: "I was shocked, surprised and outraged"
"All of GCHQ's work is carried out in accordance with a strict legal and policy framework which ensures that our activities are authorised, necessary and proportionate, and that there is rigorous oversight, including from the secretary of state, the Interception and Intelligence Services Commissioners and the Parliamentary Intelligence and Security Committee," a spokeswoman from GCHQ said.
"All our operational processes rigorously support this position."
Other details included in the latest leaks include:
GCHQ agents referred to a study that indicated Firefox users were those most prone to neuroticism, while Internet Explorer users were those most likely to be conscientious but least open to new experiences
An earlier GCHQ operation dubbed Blackhole involved exploiting what used to be unencrypted data from Twitter in order to identify users and target them with propaganda
- Published27 January 2014

- Published28 January 2014

- Published27 January 2014
