The daunting challenge of reporting on cyberwar
- Published
- comments

Welcome to the new frontline for war reporting
The US and UK are soon to take part in cyber war games - testing each other out for when the inevitable real cyberwar kicks off.
It'll be the first time such cooperation will have taken place. An unprecedented arrangement, Downing Street said, to prepare for an unprecedented challenge.
One thing's sure: the nature of war is certainly changing. And with it, so too must the way journalists report on global conflict.
Where a traditional war reporter wouldn't set out without wearing a trusty flak jacket, the war reporters of the imminent future may well be more concerned with a hardy firewall.
But there's a problem. How do you report on a war you can't see happening? How do you hold aggressors to account if you don't know who or where they are?


When reporting cyber-attacks, some of the facts may never be known
Explained: Cyber war games
The best way to test the resilience of computer security is to try and emulate the various ways hackers could break in.
That's why the US and UK are working together to essentially try and hack each other to see where the weaknesses lie.
The first war game will involve the Bank of England and commercial banks, targeting the City of London and Wall Street, and will be followed by "further exercises to test critical national infrastructure", Downing Street said.
Money will also be made available to train "the next generation" of cyber agents.
Read more: What's involved in cyber war games?

It's a concern shared by journalist Charles Arthur, who for nine years was editor of the Guardian's technology section.
"I've been writing about hackers and hacking for about 20 years and what I've noticed is that it has become increasingly difficult to verify claims," he says.
"The ability to obfuscate the source of an attack now means you can't be certain of anything you're told."
Finding the source
In conflict zones, getting hold of good information can be a mucky, imprecise business. Both sides make it their business to try and control what hits the news.
To get around such control, journalists in years gone by have had to improvise.
The most famous example, and one that's passed on to every aspiring journalist the world over, came from legendary BBC reporter Brian Hanrahan.

Legendary reporter Brian Hanrahan had to resort to inventive ways to get the news out
While reporting on the Falklands War, he faced a problem.
The Argentines had claimed they shot down British Harrier jets, but Hanrahan knew this was untrue. However, he was told by the British navy - with whom he was embedded - that he absolutely must not say how many planes were involved in an operation.
And so, in perhaps the finest piece of broadcast news scripting ever, he decided to say this: "I'm not allowed to say how many planes joined the raid.
"But I counted them all out and I counted them all back."
Hard evidence
Last week my colleague Will Ross explained, external how the only worthwhile information that reached the media about a recent Boko Haram massacre came via the hassling of a reluctant Nigerian politician, in a car park.
That probing followed what looked like mounting evidence something dreadful had occurred - the official's comments confirmed it had.
In cyberwar, you often can't see the signs. There are no planes to count in and out, no soldiers to grab and ask "who are you fighting for?".

Checking out the authenticity of everyday stories can be legally troublesome
"It's as though the journalists in Iraq in 2003 had to rely on Comical Ali, external for their information - but with nothing else, no visibility," says Charles Arthur.
"We're reporting on a war where the fog never clears, and the participants aren't visible. That puts facts at a premium."
Which is why, years on, we still don't know for sure if the US (with Israel's help) was behind Stuxnet, a cyberattack that caused physical damage to Iran's infrastructure, despite strong evidence.
We don't know if the UK was responsible for a serious hack on Belgacom, a Belgian telecoms firm, despite some putting forward what they see as proof, external, and others calling for an official inquiry, external.
And we don't know who was behind the tampering of blast furnaces in Germany last month. We don't even know who was attacked!
Cyber bogeyman
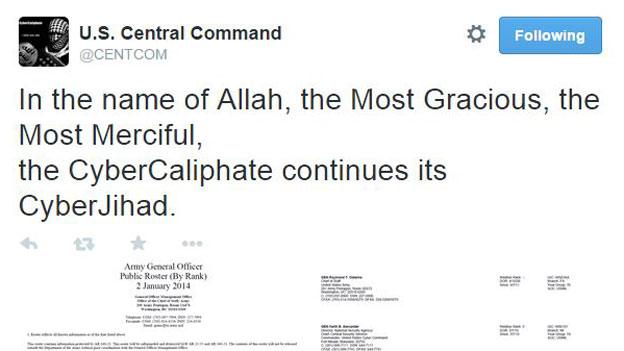
Let's look at an active story. The hack on Sony Pictures has been something of a perfect storm when it comes to highlighting the problems journalists face in reporting cyber-attacks.
Look at North Korea. Kim Jong-un is a tempting candidate for cyber-bogeyman-in-chief, but experts are queuing up - in my inbox, at least - to dispel a lot of the evidence produced by the US backing up its claims that North Korea hacked Sony.
The FBI has said it has extra, confidential information that makes it sure it is right - but the public isn't allowed to know what that evidence is.

The Sony Pictures hack exposes a gap in crucial information in reporting cyber-attacks
We - and by we, I mean the public - find ourselves in a situation where nations could go to cyberwar, and we'll just have to take our leaders' word that it's the right thing to do.
(That's assuming we're told about the cyberwar at all. Unlike "real" conflict, cyberwar doesn't require a leader to stand up in Parliament or Congress to explain what's about to happen.)
The problem in a nutshell is this: reporting on cyber-attacks currently relies far too heavily on taking what our governments say as fact.
That's not a new situation, but unlike in the past, when reporters could take steps over time to find out more, cyber-attacks occur in a manner that is unverifiable, often leaving its perpetrators unaccountable.
Snapchat hack
But that's perhaps the more extreme end of the problem. What about the day-to-day challenge?
Last year I published this: Nude 'Snapchat images' put online by hackers.
You'll notice the use of quote marks, signalling that I'm attributing the story to some other source. In this case, it was a story by Business Insider journalist James Cook, external, and beyond that, the internet at large - chat on Twitter, Reddit... all the usual suspects.
But it also means we're not quite sure if they indeed were Snapchat images. I was covering myself, and continued to do so in the article itself. "Reportedly" leaked online, I wrote.
Was it lazy journalism (as one of my followers on Twitter politely suggested)?

Reports of leaked images from Snapchat users were
It might be the first accusation, but that would be unfair - my day was spent hassling Snapchat, who eventually provided a brief response, but ignored requests for clarity, no doubt searching for answers too.
I was also grasping for any information I could from expert sources.
To use the journalistic jargon for "checking it's true" - the story was extremely difficult to stand up. It may have even been illegal to do so.
By simply making efforts to verify that a breach had occurred - i.e. finding and looking at the material posted online - I would put myself at risk of breaking laws over accessing images of minors.
Accessing material of that nature, in any circumstance, is illegal. No exceptions.
My only option was to report the story in the way I did, or face not reporting it at all - a significant failing.
Millions of people use Snapchat, and if this kind of breach is going on it should be covered - regardless if the blame lies, as it most likely did, with a third-party app.
Wiggle room
Legally, morally and technologically, journalists are in unprecedented territory and it will get worse in 2015 without a hard look at how reporters go about their work.
For example, in the aftermath of the Sony Pictures hack, Sony threatened some media outlets with legal action over handling the leaked documents. Not good, says Charles Arthur.
"I think that the blanket ban on accessing 'hacked' data works against journalists trying to establish facts.

The media's work will need to include better advice, too
"There should be some wiggle room in the law, rather like that when you come across documents in the street, that allows you to access files that have been put on the public internet.
"That would help us establish what's true and what isn't."
Of course, journalists must do more. The quality of reporting cyber-attacks in the mainstream media can be, well, patchy. I'm probably being kind.
Too many stories breathlessly type up headlines containing "biggest", "most dangerous" and "most sophisticated" without proper justification.
If we do use those words, we must anticipate that the audience will demand more: what should people do? How can we be protected? Do we need to care?
Footing each article with "experts suggest changing your passwords" won't be acceptable in 2015.
Searching for superlatives
I asked Rik Ferguson, vice president for security research at Trend Micro, for his view. It's people like him who perhaps provide part of the solution in bridging the reliable information gap.
He says improvements won't happen unless tougher questions are asked.

Journalists can sometimes overstate the capabilities of groups like Anonymous
"Journalists need to be less credulous and more probing, it's not enough to print the opinion of an 'industry spokesperson' just because he purports to be an expert.
"That opinion should be qualified, justified and challenged by the journalist until they are sure of its validity.
"I was expecting exactly this when I first started acting as a spokesperson. But I continue to be surprised at how little my views are challenged by the media, almost no-one asks me why, they're too busy looking for superlatives."
A sobering view of cyber-attack coverage - but something to aim for and get right.
We may not be able to use the exact methods Brian Hanrahan made his own - but if journalists are to report accurately on what may well be the defining story of a generation, we must at least try to adopt his spirit of improvisation.
Follow Dave Lee on Twitter @DaveLeeBBC, external
- Published15 January 2015

- Published9 January 2015

- Published14 January 2015

- Published12 January 2015
- Published12 January 2015