'Bad Rabbit' ransomware strikes Ukraine and Russia
- Published
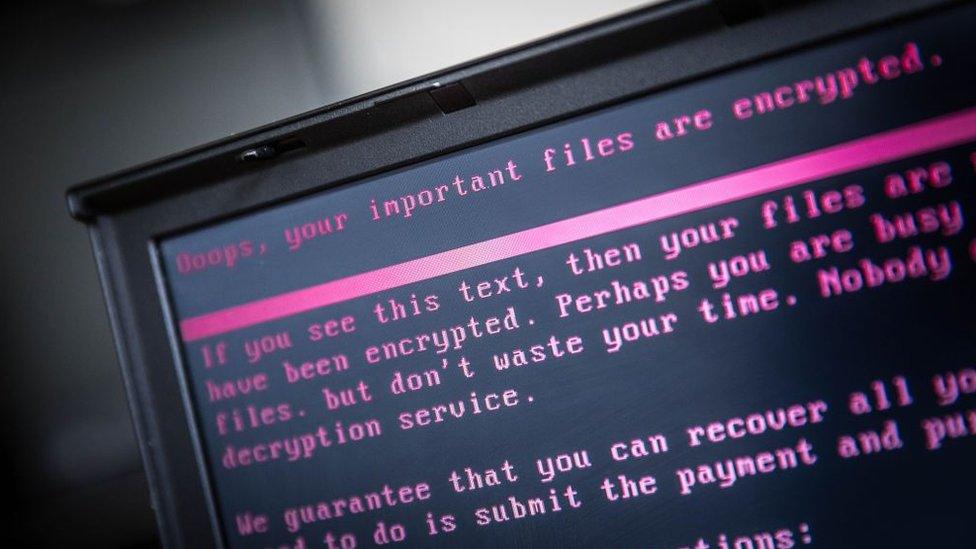
Two other ransomware outbreaks have made headlines this year - WannaCry and Petya
A new strain of ransomware nicknamed "Bad Rabbit" has been found spreading in Russia, Ukraine and elsewhere.
The malware has affected systems at three Russian websites, an airport in Ukraine and an underground railway in the capital city, Kiev.
The cyber-police chief in Ukraine confirmed to the Reuters news agency that Bad Rabbit was the ransomware in question.
It bears similarities to the WannaCry and Petya outbreaks earlier this year.
However, it is not yet known how far this new malware will be able to spread.
"In some of the companies, the work has been completely paralysed - servers and workstations are encrypted," head of Russian cyber-security firm Group-IB, Ilya Sachkov, told the TASS news agency.
Two of the affected sites are Interfax and Fontanka.ru.
Meanwhile, US officials said they had "received multiple reports of Bad Rabbit ransomware infections in many countries around the world".
The US computer emergency readiness team said it "discourages individuals and organisations from paying the ransom, as this does not guarantee that access will be restored".

Who was affected?
By Ksenia Idrisova and Yaroslava Kiryukhina, BBC Monitoring
Initial news reports mentioned Russian media websites, such as St Petersburg-based Fontanka.ru, as well as an airport in Ukraine's Odessa and a subway system in Kiev.
Privately-owned Russian news agency Interfax was hit particularly hard, to the extent that 24 hours later its website still displayed a message reading "our service is temporary unavailable".
On the morning of 25 October, it transpired that Russian banks had also been targeted but, luckily, were not compromised.
The Russian Central Bank said in a statement that it had recorded a BadRabbit attack on Russian financial institutions, but that none of them had been compromised, as reported by RNS news agency on 25 October.
Otkrytiye, formerly Russia's biggest privately-owned bank, was one of the Russian financial institutions that repelled the attack, according to RNS.
Prominent Russian IT security firm Group-IB reported that BadRabbit had targeted several of the top 20 Russian banks but failed to penetrate their networks.

Russia hit most
"According to our data, most of the victims targeted by these attacks are located in Russia," said Vyacheslav Zakorzhevsky at Kaspersky Lab.
"We have also seen similar but fewer attacks in Ukraine, Turkey and Germany."
Bad Rabbit encrypts the contents of a computer and asks for a payment - in this case 0.05 bitcoins, or about $280 (£213).
Cyber-security firms, including Russia-based Kaspersky, have said they are monitoring the attack.
Technology explained: what is ransomware?
The malware is still undetected by the majority of anti-virus programs, according to analysis by virus checking site Virus Total, external.
One security firm, Eset, has said that the malware was distributed via a bogus, external Adobe Flash update.
Researcher Kevin Beaumont has posted a screenshot, external that shows Bad Rabbit creating tasks in Windows named after the dragons Drogon and Rhaegal in TV series Game of Thrones.
The outbreak bears similarities to the WannaCry and Petya ransomware outbreaks that spread around the world causing widespread disruption earlier this year.
- Published18 July 2017

- Published28 June 2017

- Published14 May 2017

- Published14 May 2017

- Published27 October 2017
