US spy leaks: How intelligence is gathered
- Published

Documents leaked by whistleblower Edward Snowden suggest the US government has undertaken mass surveillance operations across the globe - including eavesdropping on US allies.
The claims have led US Senate's intelligence committee to pledge to review the way the country's biggest intelligence organisation - the National Security Agency (NSA) - undertakes surveillance.
According to the leaks, what are the key methods the spy agency uses?
1. Accessing internet company data

In June 2013, leaked Snowden documents revealed, external how the NSA had backdoor access to major technology companies.
The files showed the agency had access to the servers of nine internet firms, including Facebook, Google, Microsoft and Yahoo, in order to track online communication under a surveillance programme known as Prism.
They claimed the project gave the NSA - along with the UK's eavesdropping station GCHQ - access to email, chat logs, stored data, voice traffic, file transfers and social networking data.
However, the companies denied they had offered the agency "direct access" to their servers.
Some experts have also questioned Prism's real power.
Digital forensics professor Peter Sommer told the BBC such access may be more akin to a "catflap" than a "backdoor", with intelligence agencies able to tap into servers only to collect intelligence on a named target.
2. Tapping fibre optic cables
According to leaked documents from GCHQ published by the Guardian, external, the UK was tapping fibre-optic cables carrying global communications and sharing the data with the NSA, its US counterpart.
The documents showed that GCHQ was able to access 200 fibre-optic cables, giving it the ability to monitor up to 600 million communications every day.
The information on internet and phone use was allegedly stored for up to 30 days in order for it to be sifted and analysed.
GCHQ declined to comment on the claims but said its compliance with the law was "scrupulous".
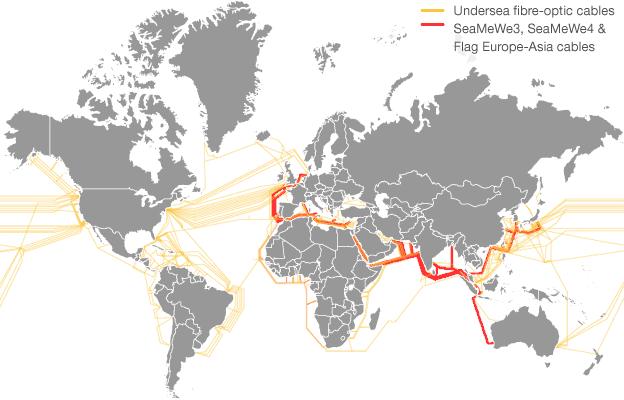
In June 2013, Italian weekly L'Espresso published claims that GCHQ and the NSA had targeted three undersea cables with terminals in Italy, intercepting commercial and military data.
The three cables in Sicily were named as SeaMeWe3, SeaMeWe4 and Flag Europe-Asia.
Then in October, the Washington Post published claims the NSA had hacked into fibre-optic cables and other network equipment, external connecting servers operated by Google and Yahoo.
According to the leaks, the agency had obtained and sifted through a wide range of material, including "metadata" - which records who sent or received e-mails and when - text, audio and video, in an operation run in conjunction with British counterpart GCHQ.
Google, which has a number of US and overseas data centres - consisting of thousands of miles of cables and computers stored in warehouses - has said it is now working to encrypt its cables.
3. Eavesdropping on phones
In June 2015, documents leaked by WikiLeaks purported to reveal US spying on three successive French presidents, external, as well as cabinet ministers and the French ambassador to the United States.
Recordings of phone conversations by Francois Hollande, Nicolas Sarkozy, and Jacques Chirac were collected by the US National Security Agency (NSA), according to the documents, which date to 2012.
The spying was "unacceptable", said Mr Hollande.
The leak echoed similar revelations October 2013, when German media reported that the US had bugged German Chancellor Angela Merkel's phone for more than a decade - and that the surveillance had only ended a few months earlier.
Der Spiegel magazine, external, again quoting documents leaked by whistleblower Edward Snowden, claimed a listening unit was based inside the US embassy in Berlin.
Investigative journalist Duncan Campbell explained in his blog, external how windowless areas on the outside of official buildings could be "radio windows". These external windows - made of a special material that does not conduct electricity - allow radio signals to pass through and reach collection and analysis equipment inside.

The German press has published claims that the US taps communications from a small windowless room at its embassy in Berlin
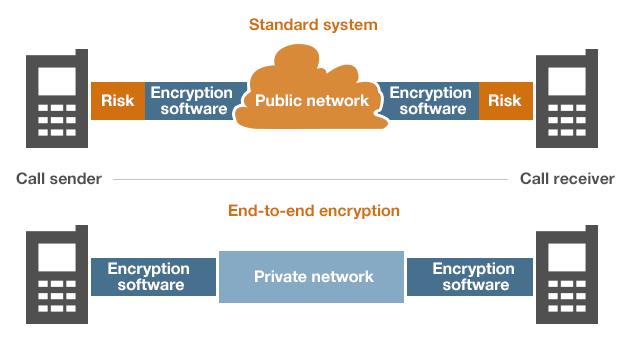
According to security experts, standard mobile phone encryption systems can be vulnerable because their scrambling system is, in software terms, separate from the program used to create a message.
It is possible for an eavesdropper to position themselves between the message-making software and the encryption system at either end of a conversation and see information before it is scrambled or after it is unscrambled.
End-to-end encryption, now adopted by many, closes this gap by having the message-making software apply the scrambling directly. In addition, many of these systems run a closed network so messages never travel over the public internet and are only decrypted when they reach their intended recipient.
How encryption systems work
As well as the bugging of the chancellor's phone, there are claims the NSA has monitored millions of telephone calls made by German and French citizens along with the emails and phone calls of the presidents of Mexico and Brazil.
The Guardian later reported that the NSA had monitored the phones of 35 world leaders, external after being given their numbers by another US government official. Again, Edward Snowden was the source of the report.
4. Targeted spying

Der Spiegel magazine published claims in June that the NSA had also spied on European Union offices in the US and Europe.
The magazine said it had seen documents leaked by Edward Snowden showing that the US had spied on EU internal computer networks in Washington and at the 27-member bloc's UN office in New York.
The files allegedly suggested that the NSA had also conducted an eavesdropping operation in a building in Brussels, where the EU Council of Ministers and the European Council were located.
Then, in July, the Guardian published claims in further leaked documents that a total of 38 embassies and missions had been "targets" of US spying operations., external
Countries targeted included France, Italy and Greece, as well as America's non-European allies such as Japan, South Korea and India, the paper said.
EU embassies and missions in New York and Washington were also said to be under surveillance.
The file is said to have detailed "an extraordinary range" of spying methods used to intercept messages. They included bugs, specialised antennae and wire taps.
5. Text message gathering
The NSA is alleged to have used SMS messages to extract data, contacts and location
In January 2014, the Guardian newspaper, external and Channel 4 News reported that the NSA collected and stored almost 200 million text messages per day across the globe.
NSA programmes codenamed Dishfire and Prefer extracted location information, contacts and financial data from SMS messages, including automated texts, such as roaming charge alerts, the newspaper said.
According to The Guardian, this was an untargeted collection of people's messages, rather than being aimed at known surveillance targets.
However, the NSA told the BBC the programme stored "lawfully collected SMS data" and any implication that collection was "arbitrary and unconstrained is false".
- Published17 January 2014

- Published1 July 2013

- Published12 June 2013

- Published16 December 2013
